SplashData unveil their most popular passwords of 2014 list
Noticia:Once again, SplashData have released their annual list of compiled stolen passwords made public throughout the year of 2014, once again showing that people really don't put much thought, time or effort into protecting their own security.
If your password is anything like these below, please change it immediately for your own safety. It's nice to see these users really confusing hackers and 'changing it up' by pushing '12345' up 17 places to a number three placing - it's definitely going to confuse those nasty criminals from guessing the old '123456' code that was set.
- 123456 (Unchanged)
- password (Unchanged)
- 12345 (Up 17)
- 12345678 (Down 1)
- qwerty (Down 1)
- 123456789 (Unchanged)
- 1234 (Up 9)
- baseball (New)
- dragon (New)
- football (New)
- 1234567 (Down 4)
- monkey (Up 5)
- letmein (Up 1)
- abc123 (Down 9)
- 11111 (Down 8)
- mustang (New)
- access (New)
- shadow (Unchanged)
- master (New)
- michael (New)
- superman (New)
- 696969 (New)
- 123123 (Down 12)
- batman (New)
- trustno1 (Down 1)
http://www.tweaktown.com/news/43003/...ist/index.html
As 7 primeiras passwords
User Tag List
 Likes: 0
Likes: 0
Resultados 226 a 240 de 955
-
21-01-15, 10:57 #226Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
-
21-01-15, 11:02 #227Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Edward Snowden: GCHQ snooped on emails sent, received by journalists
Notici:The GCHQ collected emails sent to and from journalists in the United States and UK, according to documents released by former NSA contractor Edward Snowden. It took less than 10 minutes to harvest up to 70,000 emails during the GCHQ exercise, intercepted from fiber-optic cables, and included correspondence between writers and editors.
As part of its surveillance campaign, the GCHQ archived emails related to journalists from BBC, Reuters, The New York Times, Le Monde, the Guardian, NBC, the Sun and the Washington Post - with data saved on its intranet.
It's no surprise that the NSA and GCHQ have invested in a number of different digital surveillance efforts, but the widespread campaigns have shocked critics. The GCHQ is under increased pressure to ensure journalists' emails are protected, as confidentiality is important - despite government skepticism.
"This is the inevitable result of the kind of wholesale surveillance that's now authorized under both UK and US law," said Jameel Jaffer, deputy legal director for the American Civil Liberties Union, in a statement published by the Washington Post. "There is little evidence that this kind of mass surveillance is effective or necessary, but it presents a very real threat not just to privacy but to the freedoms of speech and association as well."
http://www.tweaktown.com/news/43013/...sts/index.html
-
21-01-15, 11:37 #228
-
21-01-15, 11:43 #229Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Java software becoming more secure, as hackers target Silverlight
Noticia:Cybercriminals are always-on the lookout for software bugs they can exploit, allowing them to hopefully compromise users. Keeping software updated, for example, helps close backdoors and make it harder to find access points - but many people fail to update software, and avoid potentially preventable security incidents.
Another aspect to good cybersecurity is understanding what types of software are being targeted - and why - with clues gathered from this type of information. Java, which has been a longtime favorite for exploits, has increased focus on security, so users have shifted attention to Microsoft Silverlight. As such, experts have seen a strong uptick in Silverlight-based attacks:
"We saw a 34 percent drop in exploits in Java," said Jason Brvenik, principal engineer of security business at Cisco, in a statement to SCMagazine.com. "Java has become more secure. Attackers have noted this, so we saw a rise in the exploit of Silverlight consequently."
http://www.tweaktown.com/news/43008/...ght/index.html
-
21-01-15, 11:45 #230Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Chinese cyberattacks left Microsoft's Outlook vulnerable, reports say
Noticia:The Microsoft Outlook.com email service reportedly was breached by Chinese authorities, using a "man-in-the-middle" type attack, according to the GreatFire watchdog group.
MITM attacks typically rely on hijacked online connections used to monitor and control communications through an online communication - with email users relying on IMAP and SMTP to access Outlook, Mozilla Thunderbird and other apps left vulnerable.
"We suspect that the Cyberspace Administration of China, which is directly in charge of censorship... is directly responsible for the MITM attack against Outlook, and the recent related MITM attacks in China," according to the report.
China has used similar methods to breach Apple's iCloud service, Google's Gmail, and other online email and cloud storage solutions.
Microsoft confirmed the incident to the media: "We are aware of a small number of customers impacted by malicious routing to a server impersonating Outlook.com. If a customer sees a certificate warning, they should contact their service provider for assistance."
http://www.tweaktown.com/news/43012/...rts/index.html
-
21-01-15, 13:13 #231Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Lizard Squad's DDoS service hacked, customer details revealed
Noticia:
Lizard Squad, the hacker group that took down Xbox Live and the PlayStation Network on Christmas Day and then tried to cash in on its fame by selling the distributed denial-of-service service they used in the attacks, has received a dose of its own medicine... by getting hacked.
Online security researcher Brian Krebs claims to have accessed a customer database for LizardStresser, the tool that the hacking collective claims allows you to launch DDoS attacks on any website or internet service of your choice -- he had earlier claimed that the attacks are mostly powered by thousands of hacked home Internet routers.
“A copy of the LizardStresser customer database obtained by KrebsOnSecurity shows that it attracted more than 14,241 registered users, but only a few hundred appear to have funded accounts at the service,” Krebs said in a blog post, adding that paying customers handed over more than $11,000 in bitcoins to the group.
Krebs also noted that all registered usernames and passwords were stored in plain text, which is ironic given that the hacking group had said that the Christmas Day attacks were carried out to demonstrate poor security on Sony's and Microsoft's part.
This is the second major setback for Lizard Squad in a week, after UK’s South East Regional Organized Crime Unit (SEROCU) arrested an 18-year-old last Friday in connection with the Playstation and Xbox attacks. Two other members of the hacking group have also been rounded up by police since the initial attacks.
For those who are not in the know, this is the same group that took the responsibility for Blizzard and PlayStation Network outages last August, saying that the action wouldn't stop until the US ceased attacks on the Islamic State (also known as ISIS or ISIL).
http://www.techspot.com/news/59455-l...-revealed.html
-
21-01-15, 14:20 #232Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Putin spies on everyone in Moscow
Noticia:
For their own good of course
Moscow is to experiment with a new system of mobile-phone tracking in 2015 to "aid research into potential modification to the transport infrastructure of the city."
Basically the idea is that the authorities will monitor the movements of everyone in the city using their mobile phones. This data will identify redundant or needful traffic arrangements, as well as the provisioning of interchanges on the underground system and corresponding availability of bus services.
Of course it will mean that Tsar Putin will know where his citizens are 24 hours a day seven days a week, but that is nothing to worry about is it? The system will be augmented by GPS data in particularly dense and labyrinthine areas, such as 'old Moscow'.
Head of The Center for Traffic Management Vadim Yuriev said: "In 2015 we plan to establish a system of analysis of traffic flows based around GSM-tracks in the Moscow metropolitan area. [The system] will collect, process and analyse data on the movement of mobile subscribers in Moscow and the Moscow suburbs."
There is no evidence of 'opt out' so far reported, but the authorities claim that the anonymity of mobile-phone users will be preserved and everyone knows that Tsar Putin never lies.
To be fair Moscow is one of the world's most traffic-clogged capitals, currently home to a population of more than 11.5 million people.
Of course the 'big three' mobile providers in Moscow already cooperate extensively with Moscow authorities in providing access to the movements of its mobile subscribers.
http://www.fudzilla.com/news/36807-p...yone-in-moscow
-
21-01-15, 15:07 #233Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Pirate Bay homepage updated with traditional features
Noticia:With just 10 days left on its giant countdown timer, the Pirate Bay has made its biggest return to form since it showed up several weeks after being taken down late last year. Along with the waving black flag – which takes up a lot less space than it once did – the traditional search bar has appeared, along with links to various side projects like the Promo Bay and PirateBrowser. While text is present for many other links around the site, those two are the only ones active. The Pirate Bay cove image has also been uploaded in its full colour form now as well.
While the admins of TPB initially stated that they weren’t sure it’s return was warranted, after so many people began running their own sites using the OpenBay format, the long running torrent search site reappeared online last year after weeks of down time. Initially it displayed just a waving pirate flag and some popups if you clicked anywhere, but over time more features have been added.
Before long, a countdown appeared, pointing to the start of February as a potential relaunch of the site, or perhaps a re-imagining of what TPB could be. This was later followed by an obfuscated image of the Pirate cove, which uses the pirate analogy to geographically locate elements of the piracy debate. If zoomed in, the page would animate the Pirate Bay ship logo sailing to the island, perhaps signifying its return home.
With the addition of the search bar and (albeit mostly broken) links, the site looks almost ready to go. It is now using Cloudfare to protect its front end, but the main front-end server is now hosted in Moldovia according to TorrentFreak. The last front-end was hidden in a datacentre in Sweden, located in the side of a mountain.
http://www.kitguru.net/channel/jon-m...onal-features/
-
21-01-15, 16:06 #234Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Government Computer Linked to Hundreds of Anonymous Wikipedia Edits
Noticia:
Either someone employed at a Government facility has way to much time on his hand or some automatic process is running. One that is editing hundreds of Wikipedia entries each month, sometimes up to 90 a day and always during work hours. The edits themselves are harmless and mostly made to the fact boxes – a sidebar containing at-a-glance information on the open subject.
The fact boxes have been added to pages ranging from the Aviation Security Act 1982 to the British Homeopathic Association and on December 29th, the connection was used to make 95 edits in a single day. The unusual activity was discovered by the Twitter account WhitehallEdits that is set up by Channel 4 News to automatically tweet whenever a government owned IP address makes changes to Wikipedia.
The system has been very useful in the past and discovered the vandalism of the Hillsborough disaster Wikipedia page back in April. Now however, it has become more or less useless as the system is flooded with all these new edits every day.
Whitehall Edits @WhitehallEdits Follow
The “British Homeopathic Association” Wikipedia article was just edited anonymously from a UK government computer: http://en.wikipedia.org/w/index.php?diff=642433585&oldid=603965104 …
A spokesperson for the Cabinet Office said it was impossible to tell which computer was making the edits, or even if they were being made by a single person as public facing IP addresses can be shared by numerous computers. They also told Mirror Online that they were unable to publish information which would confirm whether this IP address had been assigned to a particular Government department, or if it was in use by a local government agency.
But the edits are following a pattern and are edited in an alphabetical order. This suggest the work of a single entity rather than a group of users as suggested.
“Civil servants are required to use their time online responsibly and follow the Civil Service Code when working online,” said the Cabinet Office spokesperson
http://www.eteknix.com/government-co...kipedia-edits/
-
21-01-15, 16:20 #235Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Law enforcement agencies have been using handheld radars to see inside homes for years
Noticia:Law enforcement agencies across the U.S. are quietly using a radar-style device that allows officers to look through walls to determine if anyone is inside a home. At least 50 agencies, including the FBI and the U.S. Marshals Service, are actively using the hi-tech tool according to a report from USA Today.
Known as the Ranger-R, the device in question looks like an advanced stud-finder that a handyman might carry. It was originally designed for use in Afghanistan and Iraq but has been used by domestic law enforcement agencies since 2012.

Priced at $6,000, it’s capable of detecting movements as slight as a human breathing from a distance greater than 50 feet using radio waves. It can penetrate most common building wall, ceiling or floor types including poured concrete, concrete block, brick, wood, stucco glass, adobe and dirt.
While its display doesn’t show a picture of what is on the other side of a wall, it is able to determine if someone is inside a house, where they are located and if they are moving.

L-3 Communications, the company that makes the Ranger-R, estimates they’ve sold around 200 units to law enforcement agencies.
Up until this past December, use of the device was largely unknown. At that time, an officer admitted to using a Ranger-R before entering a house to arrest a suspect for parole violation.

As you can imagine, its use among law enforcement has created all sorts of privacy concerns, especially since a search warrant isn’t required.
Christopher Soghoian, the American Civil Liberties Union's principal technologist, said the idea that the government can send signals through the wall of your house to figure out what’s inside is problematic. Judges overseeing its use in the parole violation arrest agreed, noting that the warrantless use of such a powerful tool poses grave Fourth Amendment questions.
http://www.techspot.com/news/59470-l...ld-radars.html
-
21-01-15, 22:33 #236Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Report: Nearly all US weapons systems in 2014 faced security issues
Noticia:The US government has increased concerns related to cybersecurity, and a new report compiled by Michael Gilmore, director of operational test and evaluation (DOT&E), likely won't help alleviate concerns. In the published 366-page report, it was discovered that almost all U.S. weapons programs tested during 2014 faced "significant vulnerabilities" related to cyberattacks.
Problems included unpatched and aging software, misconfigured network protocols, and similar issues - opening the door to potential security concerns.
"Cyber adversaries have become as serious a threat to U.S. military forces as the air, land, sea and undersea threats represented in operational testing for decades," according to the report. "The continued development of advanced cyber intrusion techniques makes it likely that determined cyber adversaries can acquire a foothold in most (Department of Defense) networks, and could be in a position to degrade important DOD missions when and if they chose to."
http://www.tweaktown.com/news/43030/...ues/index.html
-
22-01-15, 10:19 #237Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Microsoft denies Minecraft server breach
Noticia:Microsoft has denied that the disclosure of nearly two thousand account credentials for its Mojang.net service, which is responsible for the hit block-'em-up Minecraft, is indicative of a breach of its network.
Minecraft hit the news for all the wrong reasons recently when a batch of over 1,800 user accounts had their details posted publicly - including passwords in plain-text, ready to use. Although the ability to take over a user's Minecraft world isn't exactly the most tempting target for criminals, the release sparked fears that users who had reused email addresses and passwords on other services such as internet banking sites could be at risk - and that the attackers may have made off with a larger proportion of the 100 million accounts registered on Mojang.net but kept the bulk of the data secret.
Microsoft has now officially denied the latter scenario. 'We can confirm that no Mojang.net service was compromised,' the company told The Guardian in a statement on the matter, 'and that normal industry procedures for dealing with situations like this were put in place to reset passwords for the small number of affected accounts.'
Mojang was acquired by Microsoft for a whopping $2.5 billion last year, largely in response to the fantastic success of its Lego-like world-building epic Minecraft. The game has spread from PCs to consoles and mobile devices, and even has real-world merchandise in the form of physical blocks, action figures, and a themed Lego set.
Microsoft has not indicated how it thinks the usernames and passwords were obtained if not through a breach of its network, but the most likely explanation would be a phishing attack on the victims carried out via email.
http://www.bit-tech.net/news/gaming/...reach-denied/1
-
22-01-15, 10:37 #238Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Netflix gets it: piracy is competition
Noticia:While nothing is intrinsically wrong with movie studios and record labels trying to protect the content they spend a lot of money creating, they never consider piracy as direct competition for their service, seeing it instead as outright thievery. This is a very different view from the one held by media streaming firm Netflix, which sees the likes of Popcorn Time, a torrent streaming service that certainly takes a lot of cues from Netflix’s own layout and styling, as direct competitors with its services.
When Popcorn Time was launched last year, it caused quite a stir, since it took the still relatively convoluted method of pirating films and TV shows, into something that was as easy as browsing Netflix or other streaming services. This was addressed in a leter to shareholders dug up by TorrentFreak, which reads:
“Piracy continues to be one of our biggest competitors,” Netflix CEO Reed Hastings said. “This graph of Popcorn Time’s sharp rise relative to Netflix and HBO in the Netherlands, for example, is sobering,” he added.
The graph in question, is one from Google Trends, which shows that interest in Popcorn time had exploded in the past year and even mirrored the growth of Netflix itself at certain points, suggesting that their audiences are very similar.
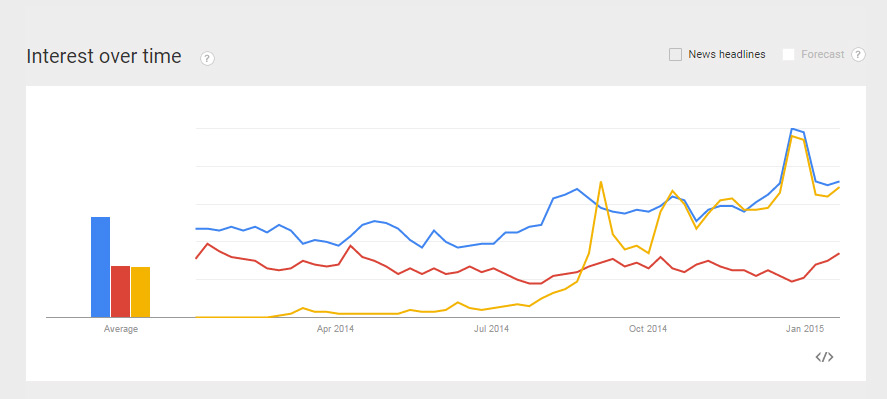
What’s important about this, is that it means Netflix is willing to consider Popcorn Time as a service that’s on the same level as its own. While clearly the piratical platform was inspired in many ways by Netflix, there is, with this attitude, the potential for that to be reversed and for Netflix to learn from Popcorn Time.
Interestingly, this represents a big change from how Netflix used to view piracy. Last year it described torrenting and other pirating services as a potential advertising tool for legitimate streaming services, since they weren’t comparable and may get people used to the idea of streaming content.
Now though Popcorn time offers something very comparable in terms of usability and a much more expanded library than Netflix can. No wonder people are worried.
http://www.kitguru.net/channel/jon-m...s-competition/
-
22-01-15, 11:00 #239Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Strongest Sign Yet That The Pirate Bay Return is Imminent
Noticia:
The new front page of The Pirate Bay homepage, thepiratebay.se, is showing its strongest indication yet the site is primed for resurrection. Below the countdown that has been a fixture since December 2014, not long after the site was taken down after Swedish police raided the site’s servers, is the familiar Pirate Search function.
The search bar and its buttons are just for show for now, but their presence suggests that they should be functional at some point in the future. The Pirate Bay is expected to make a full return on 1st February.
http://www.eteknix.com/strongest-sig...turn-imminent/
-
22-01-15, 17:01 #240Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Study: More than half or companies increased security budget by 34%
Noticia:Sixty-one percent of companies increased their cybersecurity budgets by an average of 34 percent in 2014, despite a number of high-profile data breaches still taking place, according to Identity Finder and the Ponemon Institute. Companies showed the most interest in the following security resources: Security incident and event management (SIEM), endpoint security, intrusion detection and prevention, encryption, and Web application firewalls.
Companies want to step up spending related to cybersecurity, but must ensure they are investing resources in the appropriate places. For companies breached, the information is rather frightening: 95 percent didn't discover a breach for at least three months, while 46 percent admitted they found a data incident on accident.
"This study shows that organizations are dedicating greater attention and financial resources towards managing sensitive information and preventing data breaches, which is certainly encouraging news," said Dr. Larry Ponemon, founder and chairman of the Ponemon Institute. "However, 2015 is predicted to be as bad or worse as 2014 as more sensitive and confidential data and transactions are targeted by attacks and collateral damage."
http://www.tweaktown.com/news/43049/...-34/index.html
Informação da Thread
Users Browsing this Thread
Estão neste momento 1 users a ver esta thread. (0 membros e 1 visitantes)







 Responder com Citação
Responder com Citação








Bookmarks