Kazakhstan To 'Superfish' Its Citizens; OS And Browser Vendors Could Stop ItNoticia:The Kazakhtelecom JSC, the largest telecommunications company in Kazakhstan, announced that the government will require all citizens to install a “national security certificate” starting January 1, 2016. Kakakhstan citizens will have to go to www.telecom.kz to receive a prompt on how to install that certificate on Windows, Mac OS, Android and iOS. Country-Wide "Superfish"
This would essentially mean that the government is trying to “Superfish” all of its citizens by giving itself the capability to decrypt all HTTPS traffic. The government will be able to see not just all encrypted traffic, but it will also be able to censor certain pages of content. Before HTTPS started being used by default by sites like Wikipedia, some governments would block those pages from being accessed.
Once Wikipedia and other sites moved to HTTPS, the governments had to choose whether to completely block them, or not, as it became an all or nothing proposition. Most often, at least for popular websites, they would decide not to do it, as too many people relied on them for all sorts of content.
Not using HTTPS also meant governments would see what type of content people were reading, whether in aggregate to see certain trends, or individually if they targeted anyone. With HTTPS that’s not possible anymore.
That’s why Kazakhstan, which presumably wants to maintain its censorship and surveillance powers, is now demanding all citizens to install its certificate. The “national security” reason is invoked, because that seems to make people more willing to accept it, even if the vast majority of uses of the certificate won’t be for national security purposes (or at least what is commonly regarded as actual national security, as the Kazakhstan government could interpret it however it wants, ultimately).
Security Risk
The problem even with this security argument is that it may in fact make Kazakhstan citizens less secure, not just against their own government, but against other criminals as well. We’ve learned earlier this year, with Lenovo’s Superfish and more recently with Dell’s own root certificate, that these certificates can pose a great security risk for computer users.
If hackers get ahold of the private key of that root certificate (and we can probably assume the Kazakhstan government doesn’t have world renown security in place to protect that private key), they could also use it to decrypt anyone’s communications.
It’s also going to be a very slow process to update those certificates if the government does find out its private key has been stolen. Unlike with Lenovo and Dell, which could either update the laptops themselves or rely on Microsoft to do it for them and remove those bad certificates, it could take years before most Kazakhstan citizens install the new certificate again.
How To Stop It
There are only two ways for Kazakhstan citizens to stop this now. One would be to protest against the move. The other is to ask technology companies to take measures against it by refusing to use that certificate for their services or apps.
Service providers could pin only certain certificates they can trust and not allow their sites to work with any other certificate. Browser vendors could also ban those certificates from being supported in their browsers, as they’ve already done with China’s root Certificate Authority.
Finally, the platform vendors (which are also the major browser vendors), such as Microsoft, Google and Apple, could update their operating systems to remove that certificate from their operating systems’ root stores.
They could even release future versions of their operating systems that would disallow any other root certificate than the default ones. This could annoy some power users who want to be able to test/install their own certificates, but in the vast majority of cases, consumers never try to install a root certificate themselves.
Microsoft, for instance, could still allow enterprise, or even Pro versions of Windows to install certificates. This would still protect most people against such abuses, whether from certain manufacturers’ bad certificates, or from more oppressive nation states.
http://www.tomshardware.com/news/kaz...ens,30683.html
Mau de mais
User Tag List
 Likes: 0
Likes: 0
Resultados 796 a 810 de 955
-
03-12-15, 20:41 #796Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
-
04-12-15, 13:43 #797Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Hacking a big corporation is easy
Noticia:
McAfee claims a grannie could do it
Hacking a major corporation is so easy that even an elderly grannie could do it, according to technology industry character John McAfee.
McAfee said that looking at the world’s worst hacks you can see a common pattern – they were not accomplished using the most sophisticated hacking tools.
Writing in IBTImes said that the worst attack was in 2012 attack on Saudi Aramco, one of the world's largest oil companies. Within hours, nearly 35,000 distinct computer systems had their functionality crippled or destroyed, causing a massive disruption to the world's oil supply chain. It was made possible by an employee that was fooled into clicking a bogus link sent in an email.
He said 90 per cent of hacking was social engineering, and it is the human elements in your organization that are going to determine how difficult, or how easy, it will be to hack you.
The user is the weakest link in the chain of computing trust, imperfect by nature. And all of the security software and hardware in the world will not keep a door shut if an authorized user can be convinced to open it, he said.
“Experienced hackers don't concern themselves with firewalls, anti-spyware software, anti-virus software, encryption technology. Instead they want to know whether your management personnel are frequently shuffled; whether your employees are dissatisfied; whether nepotism is tolerated; whether your IT managers have stagnated in their training and self-improvement.”Muct of this information can be picked up on the dark web and the interernet underground, he added.
“"Are you prepared for a world where grandma or anyone else can quickly obtain, on the wide open web, all of the necessary information for a social engineering hack? Is your organization prepared?” he said.
http://www.fudzilla.com/news/39395-h...ration-is-easy
-
05-12-15, 16:40 #798Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Millions Of Phones, Routers And Smart TVs Vulnerable To Old Unpatched Security Hole
Noticia:Security researchers thought that we were all rid of a pesky vulnerability that was initially patched over three years ago. The exploit takes advantage of code lurking within the “libupnp” library, which is included in the Portable SDK for UPnP Devices used for DLNA media playback.
However, some lax vendors have failed to include newer versions of the SDK with an updated version of libupnp, leaving millions of devices that we use everyday exposed -- 6.1 million devices to be exact, including smartphones, routers and smart TVs.
In addition to hardware vendors, it’s also been discovered that 547 apps use the outdated version of libupnp. Amazingly, over half, 326 apps, are available via the Google Play Store. Some of the most high-profile apps that were until recently still using the older version of libupnp include Netflix, the popular streaming app, and QQMusic, an app used by over 100 million Chinese users. QQMusic uses version of 1.6.17 of the SDK, which dates back to April 2012, while Netflix is using an even older version (1.6.13).
image: http://hothardware.com/ContentImages...p_smart_tv.jpgWhat makes libupnp so troubling is that a stack overflow can be invoked using Simple Service Discovery Protocol (SSDP) packets. Buffer overflows can then be used to cause an actual crash, but that’s not all that can be accomplished by someone skilled enough to take advantage of the exploit.

One Smart TV susceptible to the libupnp exploit (Source: Trend Micro)
“With further research an exploit could be used not just to cause a crash, but to run arbitrary code on an affected device,” said Veo Zhang of Trend Micro. “The ability to run arbitrary code would give the attacker the ability to take control of the device, as on a PC.”
While smartphone OEMs (and more specifically, U.S. carriers that often pull the strings when it comes to software updates) don’t exactly have the best track record when it comes to updating devices, researchers are most worried about routers and smart TVs, which are often updated an even more sporadic schedule.
After being contacted about the vulnerabilities by Trend Micro, QQMusic developer Tencent acknowledged and released a fix for the exploit in its Android app. Likewise, the Linphone SDK has also been patched to address the outdated library. Given the press that this issue is now receiving, we have the feeling that other app developers and OEM manufacturers are going to start issuing updates as well.
http://hothardware.com/news/millions...feKtIEzgvQc.99
-
06-12-15, 15:16 #799Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Wetherspoons Reveals Extent Of Hack
Noticia:
From phone calls made to and from prisons, to the details of thousands of children and their parents, hacks seem to be everywhere and are affecting everyone these days. The latest one to reveal they’ve been hacked is JD Wetherspoons, the popular pub chain.
Revealing that its old website was hacked between the 15th and 17th of June, but only learning about the attack on the 1st of December, Wetherspoons called in security specialists before informing customers on the 3rd of December. Yet again the hack seems to have revealed a database containing numerous customer details, currently put at around 656,723 customers.
The details included in the database were the first name, surname, date of birth and contact details such as mobile phone numbers and email addresses.
If you purchased a voucher before August 2014, the last four digits of your credit or debit card could have been accessed, although they are keen to express that no other details, such as security codes or the remainder of your card details, were exposed.
Don’t pay by card? How about not using your card when you go to Wetherspoons? This doesn’t affect me? Did you sign up for their free wifi, or maybe even used the Contact us form? If you did then your data could be included in that which was revealed.
Amongst TalkTalk, Vodafone and VTech, more and more companies are finding their systems breached. Maybe now is a good time to avoid handing out any details to any company or person.
http://www.eteknix.com/wether/
-
07-12-15, 14:27 #800Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
BitTorrent Inc. serves 200 million+ ads a day
Noticia:When it was announced back in 2012 that the Utorrent BitTorrent client was going to begin serving adverts, it wasn’t a particularly popular move. Despite that though, to this day they continue to be served in monstrous numbers. The latest count has the software’s parent company BitTorrent Inc., serving upwards of 200 million adverts per day.
This is an impressive number in its own right, even more so because it shows growth over the years. Back in 2013 we were shocked to learn that the software was serving five billion impressions per month, but a little bit of maths shows us that we’re more like six billion and change in 2015.
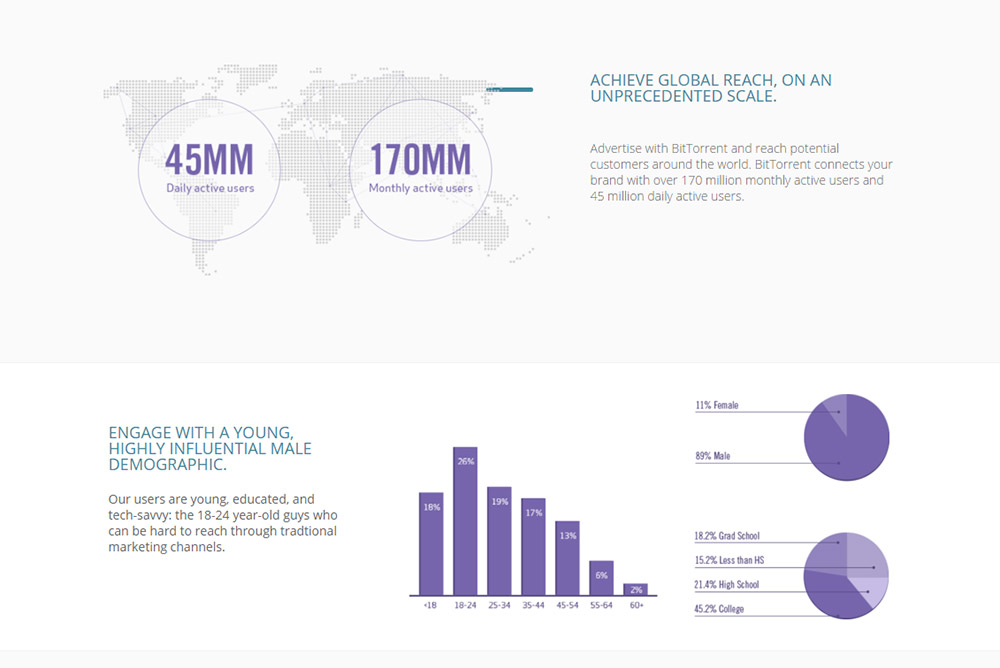
What’s perhaps more surprising though is that viewing adverts is an optional feature. Utorrent users can go into the options menu and turn them off, but most choose not to, as per TorrentFreak.
Of course despite serving so many adverts to its customers on a daily basis, it isn’t making much from them compared to other ad firms. While Youtube might be able to charge over a dollar per thousand impressions, BiTorrent Inc. is currently pushing its impressions at just seven cents per thousand.
If it manages to sell all of them it’s still making $14,000 (£9,000) per day, which is decent, but not exactly industry dominating. It’s all because of the platform too, with torrent’s links with piracy. Traditionally a cheap source of advertising like this that targets men, mostly aged between 18 and 24, 45 per cent of whom have college education, would be jumped on by high profile advertisers.
http://www.kitguru.net/channel/jon-m...ion-ads-a-day/
-
07-12-15, 18:29 #801Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Windows Pre-Boot Malware Puts Financial Industry At Risk
Noticia: BOOTRASH injection processSecurity researchers from FireEye discovered Windows pre-boot malware (or bootkit) on the machines of a customer from the financial transactions market. FireEye believes the malware belongs to a financial crime group from Russia, called FIN1.
BOOTRASH injection processSecurity researchers from FireEye discovered Windows pre-boot malware (or bootkit) on the machines of a customer from the financial transactions market. FireEye believes the malware belongs to a financial crime group from Russia, called FIN1.
“We identified the presence of a financially motivated threat group that we track as FIN1, whose activity at the organisation dated back several years,” FireEye reported. ”The threat group deployed numerous malicious files and utilities, all of which were part of a malware ecosystem referred to as ‘Nemesis’ by the malware developer(s).”A “bootkit” can infect lower-level system components, which makes identifying it quite difficult. It’s also highly persistent and will not be removed by re-installing the Windows operating system. The malware supports a wide array of backdoors and capabilities, which include file transfer, screen capture, keystroke logging, process injection, process manipulation, and task scheduling support.
Once a target computer is infected with the Nemesis malware, it can be further updated to include more hacking tools and functionality. In early 2015, the FIN1 group updated Nemesis to include a utility that modifies the Volume Boot Record (VBR) and hijacks the system boot process to begin loading malware components before Windows system code. FireEye called this utility BOOTRASH.
BOOTRASH hijacks the boot system through a multi-step process, in which it creates a virtual file system in the unallocated drive space between partitions. It then hijacks the original VBR code with its own infected code. The malicious code then injects 32- or 64-bit versions of the Nemesis components into the Windows kernel.
The BOOTRASH installer will work with any drive that has a Master Boot Record (MBR) boot partition, but it will not work with the GUID Partition Table (GPT) disk architecture. It’s also unlikely that it will work with Windows machines that use Secure Boot, which is meant to protect against this type of bootkit and uses GPT as a requirement, as well.
Interestingly enough, the malware also needs the .NET 3.5 or later framework to work; otherwise, it will quit working. This seems like a considerable weakness in the portability of the malware. However, most Windows machines, especially from enterprise customers, should also have the .NET framework installed for use with other applications.
According to FireEye, bootkits aren’t that common, but there have been reports of such malware in the past. The bootkits have usually targeted the financial industry, but other industries have been affected as well. Their pre-boot persistence in enterprise computers makes them appealing to attackers. They also seem to be used when other techniques don’t work so well or when the targeted data is of high value.
FireEye suggested that re-installing the operating system is no longer a sufficient method of getting rid of certain types of malware. The solution against this type of threat is to use tools that can access and search raw disks at scale for evidence of bootkits, or the disks should be physically wiped before installing the operating system.
http://www.tomshardware.com/news/win...try,30703.html
-
08-12-15, 15:15 #802Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Linksys-routers Vulnerable due to multiple cgi-scripts
Noticia:Linksys routers ranging from model EA6100 up-to EA6300 are Vulnerable and exploitable due to multiple cgi-scripts. The scripts can be used by an unauthorized attacker, which can get them access to the master password of the device.
Linksys' EA6100-6300 wireless routers will need a patch reports the register: KoreLogic has published an advisory saying that CGI scripts in the admin interface open the device up to remote attackers. Since it's a consumer product the risk is high that most of the devices out there never would be patched. The bad scripts include the bootloader, sysinfo.cgi, ezwifi_cfg.cgi, qos_info.cgi and others.
The disclosure is attributed to Matt Bergin of KoreLogic. His proof-of-concept code provided with the advisory includes testing the target device to see if its admin password remains set to default. At the time of writing, Linksys has not published a fix, so it's at the very least recommended to shut down remote admin access to any devices you're in contact with.
http://www.guru3d.com/news-story/lin...i-scripts.html
-
09-12-15, 15:09 #803Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Nexus Mods suffers security breach, password changes advised
Noticia:Yet another site has suffered a security breach, putting user information at risk. This time, the popular modding site, Nexus Mods, has been affected, with the site admins now advising users to change their passwords. Several popular mods were altered during the breach, with a new a new file called ‘dsound.dll’ added. Those mods were taken offline while the breach was being fixed and the original files have since been restored.
However, this does mean that security has suffered a breach. Right now, apparently user accounts registered before mid-2013 are affected and potentially had their passwords accessed. However, even if your Nexus account is newer, a password change is recommended.

Unfortunately, while the breach has been fixed, right now the people behind Nexus Mods don’t know exactly when or why the breach occured, so if you downloaded the Higher Settlement Budget, Rename Dogmeat or the BetterBuild mods for Fallout 4, you may want to remove those files.
Right now, Higher Settlement Budget has been fixed and is back online but the other two have still been pulled for the time being. It doesn’t look like any payment information for Nexus Premium was accessed.
http://www.kitguru.net/gaming/securi...anges-advised/
-
09-12-15, 15:12 #804Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Government cyber-crime agency paints all teens as hackers
Noticia:With the way the media loves to pump fear into everyday citizens, it’s no wonder that guidelines for ‘how to spot your teen doing X’ are a common bit of advice dished out by various organisations. The latest advice guide from the National Crime Agency (NCA) however, has such loose ideas of what a hacker may be like, that they practically paint every young computer user as a potential criminal mastermind.
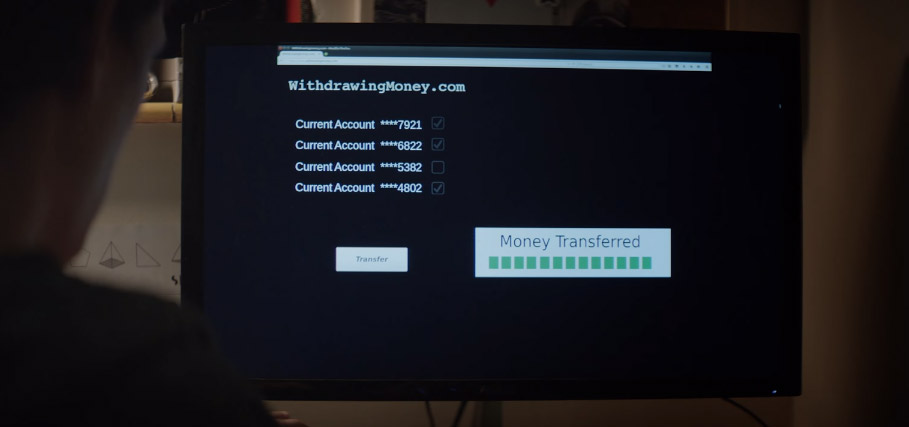
The NCA actually bought “WithdrawingMoney.com.” It sends you to the official site.
In the new initiative titled Cyber crime: Preventing young people from getting involved, the NCA asks and answers questions like “what is cyber crime?” and ‘what are its consequences?’ Those are relatively innocuous, breaking down what hacking, DDoS attacks and malware creation are, as well as what these various activities can lead to – namely criminal charges.
However it’s in the “Warning signs of cyber crime,” section that things get a little silly. The idea is to teach parents what some of the things their child might do if they are taking part in hacking or malware making themselves. Things like, “spending all of their time online,” or showing an interest in coding, including “having independent learning material on computing.”
While you could see how these sorts of activities might relate to a young person who is looking into hacking and data security, it also sounds like someone who could potentially be one of the security experts that there is such a shortage of in IT. Similarly so, independent learning is something to be encouraged, not looked on with suspicion.
The most ridiculous on the list however is the warning that your child might be a hacker if they “use the full data allowance on the home broadband.” Downloading malware kits or hacking services isn’t going to use a lot of bandwidth. More likely the kid has just figured out they can get Netflix in their room.
Admittedly the NCA doesn’t suggest that parents who discover their child has “irregular sleep patterns,” should call the police, but have a chat with their child to gauge their computer skill level. Something tells us that if parents are reading this page however, they won’t understand if their kid is particularly skilled, especially at security.
The NCA does also point out some of the positive ways that this sort of research and knowledge can be funnelled though. The Cyber Security Challenge is one way, as wall as tech apprenticeships and the Inspired Careers hub.
http://www.kitguru.net/gaming/securi...ns-as-hackers/
-
09-12-15, 15:45 #805Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
University Network “Janet” Struck by Cyber Attack
Noticia:
Universities in the UK have been struck by a DDOS attack which caused major outages to the Janet network. This network serves over 18 million users and provides UK education bodies with a highly reliable and supposedly secure network. The cyber attacks “have resulted in reduced connectivity and disruption” in a statement on network provider, Jisc’s Facebook page. Jisc executive director Tim Kidd explained:
“We understand the importance of connectivity to colleges, universities and other public sector organisations,”According to the BBC, the University of Manchester sent out an e-mail after hearing complains from staff and students about connectivity problems which reads:
“We are doing everything in our power to ensure normal service in resumed as soon as possible, and in the meantime to minimise any disruption that users of the Janet network may be experiencing. We apologise for any inconvenience caused.”
“By flooding the service with excessive network traffic, an attacker is attempting to exceed the capacity of the service, which causes the service to run slowly or become unavailable,”Apparently, the DDOS attacks have managed to disrupt the Janet network for two days and counting! This isn’t an ideal situation and means many students cannot complete their coursework or look online for reading materials. Realistically, you wouldn’t expect a huge government funded network to fall so easily to a DDOS attack and illustrates the system’s vulnerabilities. Hopefully, the network team can learn from this escapade and find better ways to fight cyber attacks in the future. It’s quite clear though that DDOS attacks are on the rise.
http://www.eteknix.com/university-nety-cyber-attack/
-
09-12-15, 15:47 #806Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
FBI Admits Use of Zero-Day Exploits and Stingrays
Noticia:
In a profile of Amy Hess, the FBI’s executive assistant director for science and technology and overseer of the bureau’s Operational Technology Division, conducted by the Washington Post in the wake of the San Bernardino shootings, the FBI executive openly admitted to the use of a number of techniques the FBI use in order to track down criminals. Amongst the methods brought to light by reporter Ellen Nakashima are Zero-Day Exploits, Stingrays and the OTD’s Remote Operations Unit of hacking technicians.
For those unaware, a Stingray is a type of “cell-site simulator” that imitate cellular towers, in order to collect communications data from mobile telephones within range, both suspect and bystander alike. The tool has been a long-kept secret by the FBI, with them requiring local law enforcement members involved in their use to sign nondisclosure agreements. While Hess insisted that the FBI never enacted a gag on the police, they wanted to keep the details of the device’s functionality shielded.
A zero-day exploit is a flaw in a piece of software that can be manipulated in order to exploit it in some way, that are unknown to the software’s vendor and thus unpatched. Usage of these can allow for easier hacks into suspects PCs or mobile devices, however favoring such techniques is unreliable, and thus not a preferred method to use.
The real worry with these types of attacks are the privacy implications on the common person. A stingray’s data would have to be checked in order to identify the suspect’s data, meaning that the privacy of everyone within proximity of the device potentially has their privacy violated. Holding on to known exploits instead of reporting them to the software developers for patching opens any user of the software open to attack from a hacker were the exploit discovered by another unsavory party. As a result of these implications, both are seen as controversial by privacy advocates and as a result, governments have often tried to distance themselves from discussion of their use. Now, in an unusual moment of transparency, the FBI has potentially put itself a little closer to the disc
http://www.eteknix.com/fbi-admits-us...its-stingrays/
-
10-12-15, 14:04 #807Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
U.S. state official admits hacking and online stalking women
Noticia:A former member of the United States’ State Department working at the embassy in London, has pleaded guilty to attempting to extort hundreds of women to send him sexually explicit images. He used data and pictures he copied from various email and social networking accounts, after phishing login details from his potential victims.
The court was told that 36 year old Michael Ford would send emails posing as members of technical support teams for various email providers and social networking firms in order to obtain account details from the women – most of whom were attending American colleges.

‘What’s that James? No I was just… just, getting some pictures. Yea.’
He specifically asked for footage of them getting undressed in public changing rooms, but demanded a variety of sexually explicit photos and videos in exchange for not sharing the information and pictures he obtained.
In cases where Ford was unsuccessful in coercing more images from his victims, he would often resort to threats. The courts were told that he would sometimes remind women that he knew where they lived, or send photos he had found within their accounts to friends and family.
Ultimately he pleaded guilty to nine counts of cyberstalking, seven counts of computer hacking to extort and one count of wire fraud (as per Reuters).
http://www.kitguru.net/gaming/securi...talking-women/
-
10-12-15, 14:47 #808Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Large Scale DDoS Attempted Take Down of DNS Root Servers
Noticia:
Someone actually tried the impossible on two separate occasions, to take down the internet’s backbone. They did ultimately fail for multiple reasons, but at the same time, they actually got a surprisingly good result out of their attack.
Early last week the Internet’s DNS Root Servers, that are the authoritative reference for mapping domain names to IP addresses, were hit with a flood of as many as 5 million queries per second for up to three hours with the goal to crash the servers. The Distributed Denial of Service (DDoS) attack took place on November the 30th and December the 1st.
The DDoS attack effectively managed to take 3 of the 13 DNS Root Servers offline for a couple of hours which in itself is quite impressive. It does however not have any real effect on the world due to the nature of DNS’ structure. DNS servers are built up in a mesh structure which means that you’ll need to take down all of them at the same time to have any real effect. And that includes the thousands of DNS servers that users connect to from their ISPs as well as all the public ones. Should the request to one DNS server fail, another will jump in and you’ll merely have a minor delay and no breakdown.
According to an analysis published by the root server operators on Tuesday, each attack fired up to 5 million queries per second per DNS root name server, and that was enough to flood the network and cause timeouts on the B, C, G, and H root servers.
At this time, there is no indication of who or what was behind this large-scale DDoS attacks. The source IP addresses used in the attacks were very well distributed and randomized across the entire IPv4 address space, so there is no clue to go by. The same goes for the motive, maybe it was a ‘let’s see if we can do it’ thing.
http://www.eteknix.com/large-scale-d...-root-servers/
-
12-12-15, 14:59 #809Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
One in three pirate sites contain malware, report finds
Noticia:
Using torrent sites is risky business, and I'm not just talking about the legality of downloading copyrighted material. According to a joint report from Digital Citizens Alliance and RiskIQ, users are 28 times more likely to contract malware from a torrent site compared to mainstream websites or licensed content providers.
In a sample of 800 sites that distribute copyrighted movies and television shows, RiskIQ found that one in three pirating sites contained malware. What's more, 45 percent of the malware detected was of the drive-by type meaning visitors don't even have to click a link to become infected.
Of the malware it encountered, RiskIQ said 54 percent was trojans while 29 percent was adware. The remaining 17 percent consisted of toolbars (five percent), botnets (three percent) and "other" (nine percent).

Some may wonder why torrent site administrators (or anyone in general) would have an interest in loading a site with malware. The answer to that question is really quite simple as it all comes down to money.
As the report notes, there's a lot of organized crime at play in which crime rings will recruit torrent site owners to help them spread malware. It's estimated that pirate site owners generate as much as $70 million each year from such crime units. That may seem like a lot of money but it's hardly anything at all compared to what stolen credentials are worth.
Need proof? The Department of Justice claims that US consumers lost $24.7 billion to identity theft in 2012.
http://www.techspot.com/news/63116-o...ort-finds.html
-
14-12-15, 14:29 #810Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Hackers might be business rivals
Noticia:
Dueling with DDOS as weapon of choice
While everyone is claiming that hackers are Isis, anonymous or Chinese spooks, it is increasingly looking like a big chunk is just businesses trying to shut down competition.
A new report from Kaspersky Lab and B2B International, found that nearly half of the companies surveyed believe they know the identity and motivation of those behind recent Distributed Denial of Service (DDoS) attacks against them, with many naming competitors as key culprits.
Criminals seeking to disrupt a company’s operations make up over a quarter (28 per cent) of the suspects but a 12 per cent of companies believe that their competitors are responsible and have paid for DDoS attacks against them.
This suspicion increases even more for those in the business services industry, with over a third surveyed (38 per cent) believing that their competitors were behind a DDoS attack.
Other attackers included criminals seeking to disrupt or distract while another attack took place (18 per cent); criminals seeking to disrupt their services for a ransom (17 per cent); political activists (11 per cent); and governments or state powers (5 per cent).
Ransom is getting to be a popular method of attack according to manufacturers (27 per cent) and those in the telecoms industry (27 per cent).
Evgeny Vigovsky, Head of Kaspersky DDoS Protection, Kaspersky Lab said that DDoS attacks were no longer just about cyber-criminals seeking to halt a company’s operations.
“Businesses are becoming suspicious of each other and there is a real concern that many companies – including small and medium-sized ones – are being affected by the underhand tactics of their competitors, who are commissioning DDoS attacks directly against them, damaging their operations and reputation,” he said.
http://www.fudzilla.com/news/39456-h...usiness-rivals
Informação da Thread
Users Browsing this Thread
Estão neste momento 3 users a ver esta thread. (0 membros e 3 visitantes)






 Responder com Citação
Responder com Citação
Bookmarks