US Government department still hasn't notified all of its hack victimsNoticia:A recent hack and theft of Government files sent a US Government department into a frenzy in recent past, with further developments urging a spokesperson to inform the public that not every victim has or will be notified of this data breach just yet.
While the Government is meant to be notifying each victim of this breach from May 2014, around 7 percent of the 1.5 million people in danger are currently unable to be contacted. This is said to be due to them moving house or being without a Government-recorded address. Confirmed by the Office of Personnel Management, being the place that was hacked, this notification system is obviously not flawless.
The original hack was traced back to China but wasn't discovered or announced until one year after its occurrence, with the names, addresses, social security numbers and various other pieces of information about employees, contractors and job applicants being now in the hands of an unverified source.
http://www.tweaktown.com/news/48953/...ims/index.html
User Tag List
 Likes: 0
Likes: 0
Resultados 811 a 825 de 955
-
14-12-15, 14:40 #811Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
-
14-12-15, 17:39 #812Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Sensitive Data of Over 13 Million MacKeeper Users At Risk
The infamous MacKeeper is making the headlines again, not for any good reason too. A security researcher has claimed to have managed to download private user data of over 13 million MacKeeper accounts.
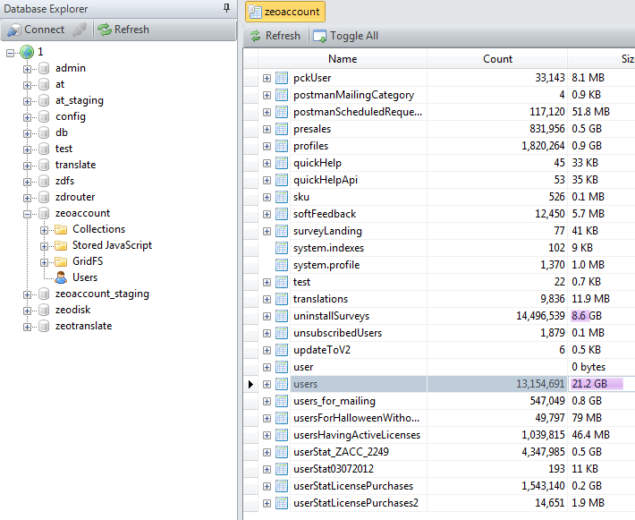
MacKeeper reported to be leaking user data:
Thanks to the company that has never been trusted for its security, integrity or even honesty with its consumers, over 13 million OS X users’ data is allegedly at risk. Chris Vickery, a white hat hacker who has previously exposed security breaches at MLB, ATP, Slipknot, and many Californian schools has reported that he was able to download the sensitive data due to the poor security system of the software suite.
I have recently downloaded over 13 million sensitive account details related to MacKeeper, Zeobit, and/or Kromtech […] stuff like names, email addresses, usernames, password hashes, computer name, ip address, software license and activation codes, type of hardware (ex: “macbook pro”), type of subscriptions, phone numbers and computer serial numbers.MacKeeper has remained in the news (mostly at the wrong end of it) for its aggressive marketing tactics, false advertising, poor user experience, and most of the time conning users for their money. There have been several times in the past when security industry has suggested OS X users to delete the suite completely. However, it was turned out that even after deleting the software, it managed to leave various traces behind.
If Vickery is right about the amount of data, he was so easily able to download, it might just prove to be the last blow for the software suite. Vickery shared on Reddit that he discovered that the three servers owned by MacKeeper, Kromtech and Zeobit have all been leaking data. He also found MacKeeper’s server to be completely unprotected,
Six hours after making this post (and it being at the top of the Apple subreddit), the database is still completely unprotected […] No log in required at all.Claiming to speed up your Mac, it mostly behaves as a malware than a helpful tool. You can read more about it on this Reddit thread.
Advertisements
Update: researcher has updated the thread with responses from the concerned companies:
UPDATE: Was contacted by Kromtech and was able to provide details to them. The database is now secure.
UPDATE 2: I have discovered 3 additional IP addresses that this data is leaking from. Kromtech has been notified and they are in the process of securing the data (again).
UPDATE 3: Kromtech believes everything is now secure.
-
15-12-15, 14:49 #813Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
UK ISPs to block 85 more pirate sites
Noticia:The UK High Court has once again ordered internet service providers to expand its list of blocked sites, with a new wave of 85 sites set to be blocked this week on the likes of Sky, Virgin Media, BT and TalkTalk. This will be one of the larger ban waves to hit recently, though most of the sites affected will likely return with a tweaked URL.
The blocks are largely focussed on torrent sites, though there are some MP3 sites also thrown in there. A lot of the blocked sites will also include mirrored domains or proxies to some of the larger torrent sites, like The Pirate Bay, KickAss Torrents or Extra Torrent.

UK ISPs have been placing these blocks in waves since 2012 and every time, more mirrors and proxy sites pop up, so this just seems to be another round of that, though it may discourage some, it certainly won’t have much of an effect on experienced torrent users.
TorrentFreak has the full list of domains set to be blocked, though the bulk of it does centre on The Pirate Bay specifically.
http://www.kitguru.net/channel/gener...-pirate-sites/
-
15-12-15, 14:54 #814Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Alleged VTech hacker arrested over six million children profile leak
Noticia:The person allegedly behind the recent hack of several million children’s accounts on the VTech Innotab tablet has been arrested. The 21 year old from the UK was said to have exposed information, pictures and audio recordings of as many as 6.4 million children and their parents after cracking the tablet’s security and taking hold of accounts and the server where they were stored.
The original hack of the Innotab and its connected services took place in November this year, though VTech didn’t find out about it until journalists alerted it to the issue. It then confirmed that several million users had been affected, with their personal information, photos and audio copied away from unsecured servers.

All Tiny Tim wanted for Christmas as an Innotab too…
“A 21-year-old man was arrested this morning in Bracknell on suspicion of unauthorised access to computer to facilitate the commission of an offence, contrary to section 2 of the Computer Misuse Act 1990 and suspicion of causing a computer to perform function to secure/enable unauthorised access to a program/data, contrary to section 1 of the Computer Misuse Act 1990,” a statement from the Thames Valley police said (via Wired).
The police are also said to have seized computers and other electronics as part of the arrest, so investigation into those items will truly decide whether this person was responsible for the hack. It may also turf up information on anyone that helped the man if he is found guilty. Indeed international organisations have been looking into the hack of the Hong Kong toy company, so it may be that a larger team of individuals was involved.
http://www.kitguru.net/laptops/table...-profile-leak/
-
16-12-15, 09:35 #815Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Police arrest 21-year-old UK man in connection with VTech hack
Noticia:
Police in the UK have arrested a 21-year-old man in connection with the recent hack of children's toy maker VTech.
Officers from the South East Regional Organized Crime Unit (SEROCU) apprehended the individual in Bracknell, Berkshire, on suspicion of unauthorized access to computer(s) to facilitate the commission of an offense and suspicion of causing a computer to perform unauthorized access to data - both part of the Computer Misuse Act 1990.
Authorities seized multiple electronic items for examination by the agency's forensics unit.
Craig Jones, Head of the Cyber Crime Unit at SEROCU, cautioned that they're still in the early stages of the investigation and there's a lot of work to be done.
News of the security breach was first reported late last month. In a series of interviews with Motherboard, the alleged hacker said he used a known SQL injection technique to gain access to the company's web and database servers. VTech only became aware of the breach after a journalist asked about the incident.
Data including names, e-mail addresses, passwords, mailing addresses and IP addresses belonging to more than six million people was compromised (no payment card information was accessed). The alleged attacker later revealed that he also made away with a large amount of photos and chat logs, many involving children.
http://www.techspot.com/news/63153-p...onnection.html
-
16-12-15, 18:15 #816Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Target Hit With Another Security Vulnerability Exposing Consumers’ Personal Data
Last year Target’s security systems were breached by hackers which led to the leak of credit card information of over 70 million consumers. Earlier this year, personal data of over 15 million of Target consumers was exposed in a security breach of Experian, a vendor that processes T-Mobile’s credit applications. Minnesota-based retailer is back in the news again for leaking private information of its consumers thanks to a flaw in the retailer’s mobile app.

Target mobile app vulnerable to hackers:
Did you choose to share your Christmas wishlist with Target mobile app? While Santa Claus may not be able to get you those gifts, Target is certainly making sure that it is known by others, more unwanted people. In a blog post, security researchers from Avast have revealed a flaw in the company’s mobile app that allows unauthorized access to customer’s private information, including email addresses, shipping addresses and phone numbers extracted from wish lists created with the app. This time it doesn’t reveal the credit card information though keeping your finances more secure.
According to the blog post, the app’s API is easily accessible over the Internet and doesn’t require any authentication:
Advertisements
To our surprise, we discovered that the Target app’s Application Program Interface (API) is easily accessible over the Internet. An API is a set of conditions where if you ask a question it sends the answer. Also, the Target API does not require any authentication. The only thing you need in order to parse all of the data automatically is to figure out how the user ID is generated. Once you have that figured out, all the data is served to you on a silver platter in a JSON file.After the report went live, Target disabled the wish list feature from the app after being informed of the vulnerability. “We apologize for any challenges guests may be facing while trying to access their registry. Our teams are working diligently overnight to resume full functionality,” Molly Snyder, communications manager at Target commented. While there’s no information if this flaw in the mobile app has been exploited by the hackers, it is unknown as to why Avast didn’t notify Target before making the details public.
The JSON file we requested from Target’s API contained interesting data, like users’ names, email addresses, shipping addresses, phone numbers, the type of registries, and the items on the registries. We did not store any personal information, but we did aggregate data from 5,000 inputs, enough for statistical analysis.
Source
-
17-12-15, 14:53 #817Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Hacker Hotz builds a driverless car
Noticia:
Hacks his own car to do it
The bloke who was the first to jail break the iPhone, George Hotz hacked his own car to turn it into a self-driving vehicle.
According to Bloomberg Hotz invited around one of their hacks to admire his handy-work.
Hotz stuck a laser-based radar (lidar) system on the roof of his white 2016 Acura ILX and a camera mounted near the rear-view mirror. A tangle of electronics is attached to a wooden board where the glove compartment used to be, a joystick protrudes where you’d usually find a gearshift, and a 21.5-inch screen is attached to the centre of the dash. It runs on Linux operating system.
Known as “geohot,” Hotz was the first person to hack Apple’s iPhone and the Sony PlayStation 3. He was unsure what he wanted to do next and decided a self-driving car idea. After all, one bloke’s ideas against expensive teams from Apple, Google and Tesla is very hackerish.
Bloomberg says it works, sort of, but given Hotz did it on his own it is not bad. It works on the highway and did steer correctly around a steep corner and avoid an oncoming SUV. We suspect the authorties will not be happy with Holtz test drive.
http://www.fudzilla.com/news/39482-h...driverless-car
-
17-12-15, 15:27 #818Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Avast investigation into shopping apps reveals another Target security blunder
Noticia:Security researchers with Avast recently took a look at several shopping apps to see just how much retailers know about their shoppers. What the team found was a bit alarming, to say the least.
Target's shopping app was among those randomly selected for a closer look. Avast discovered that data collected as part of the app's Christmas wish list feature was easily accessible via the Internet. The problem, it seems, is that Target's API didn't require any sort of authentication. Once they figured out how user IDs were generated, the team said the data was served up on a silver platter in a JSON file.

The wish list feature collected data including names, addresses, e-mail addresses, phone numbers, types of gift registries they may have signed up for and items on said registries.
Using a sampling of data, Avast was able to determine that the most popular brand on peoples' list was made by Gerber, that people using the app were most likely to live in California and Texas and that the most popular name among users was Jasmine.
Target wasn't the only retailer taking part in questionable practices. Avast found that the Walgreens mobile app requested the most unnecessary permissions of any app it examined. The Home Depot app came in at a close second, we're told.
Curiously enough, Avast didn't alert Target to the security issue before publishing its report. As CNET points out, Target shut down certain elements of its wish list feature after learning of the breach.
http://www.techspot.com/news/63172-a...-security.html
-
18-12-15, 14:15 #819Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
UK pirates sentenced to multiple year prison sentences
Noticia:Although the music and movie industry have largely stopped going after individual pirates with lawsuits – unless you’re the makers of Dallas Buyers Club – it hasn’t stopped trying to take down those responsible for uploading content. In the finale of arrests made in early 2013, four men from the UK have been sentenced to a combined 17 years in jail.
The men were of various ages, ranging from 40 to 22, but were all related to various release groups like RemixHD, 26K, UNIQUE, DTRG and HOPE/RESISTANCE (as per TorrentFreak). Although they were arrested in February 2013 though, it took until January this year before they all admitted guilt to sharing unlicensed content and conspiracy to defraud.

Source: Wikimedia
According to FACT, the British arm of the MPAA that was conducting much of the investigation, the various groups shared over 9,000 movies between March 2010 and January 2014. Although it was claimed that £52 million was lost by the industry, the various pirates only ever admitted to being responsible for £5 million in losses, which FACT accepted.
The various sentences for the individuals were as follows:
- Sahil Rafiq: four years and six months.
- Reece Baker: four years and two months.
- Graeme Reide: three years and six months.
- Ben Cooper: three years and six months.
- Scott Hemming was the only one to avoid direct jail time and was given a two year suspended sentence.
Some of these sentences may be reduced however, as one unnamed source claimed that for those that admitted guilty right away, a third of their sentence would be knocked off.
FACT is understandably pretty pumped at this result and released a statement saying that this was the first time a big release group had been successfully prosecuted.
“The result of this case sends out a serious message to anyone engaging in online piracy to think twice or face getting caught, prosecuted and sent to prison.”
http://www.kitguru.net/channel/jon-m...son-sentences/
-
20-12-15, 14:02 #820Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Juniper Networks VPN Firewall security breach probed by the FBI
Noticia:Juniper Networks has had quite the week. On Thursday it seems that some unauthorized code was found to have been inserted into their ScreenOS, which forms the basis for their hardware filewalls. This malicious code would allow a backdoor into the firewall, letting potential attackers decrypt VPN traffic with the keys found inside.
The fun doesn't stop there, however. Now the FBI has now gotten involved and will be investigating the possibility of whether foreign governments had been involved with inserting the malicious code for the purposes of intercepting encrypted communications from government employees.
And even in the non-governmental sector, Juniper is a widely used brand of IT security products, so it can't be ruled out that it was a privately funded and conducted attack with motivations not tied to any government.
Thankfully, security patches have been issued that fix this issue, and there is currently no evidence that this particular exploit had ever been used. Though we might never know due to how clever individuals could hide their tracks very easily with this code installed.
http://www.tweaktown.com/news/49100/...fbi/index.html
-
20-12-15, 14:19 #821Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Pirate Bay Founder Has Built the Ultimate Piracy Machine
Noticia:
Peter Sunde has already served prison time for his part in co-founding The Pirate Bay, but that hasn’t stopped him from creating a piracy machine that could conceivably cost him $10 million a day in copyright infringement damages. Sunde has built the “Kopimashin”, a system that copies Gnarls Barkley ‘Crazy’ 100 times per second, as an art project to show the absurdity of right’s holders claiming that piracy is robbing them of money.
The “Kopimashin”, powered by a Raspberry Pi, a LCD screen, and a few lines of Python code, creates over 8 million copies of ‘Crazy’ every day, or around $10 million in “losses” for Downtown Records and Warner Music. These copies, though, are not stored, and are instead sent to /dev/null after their creation. The act of copying itself, however, is legally seen as an infringement.
“I want to show the absurdity on the process of putting a value to a copy. The machine is made to be very blunt and open about the fact that it’s not a danger to any industry at all,”Sunde added:
“But following their rhetoric and mindset it will bankrupt them. I want to show with a physical example – that also is really beautiful in its own way – that putting a price to a copy is futile.”
“The damages in the TPB case are equally ludicrous of course. The idea behind it is of course never to get that money paid, but to scare people into silence and obedience,”The Kopimashin will be on display at an upcoming exhibition held by ‘hacker art’ organisation Konstfack, as part of the PSK value series.
Image courtesy of International Business Times.
http://www.eteknix.com/pirate-bay-fo...iracy-machine/
-
21-12-15, 14:38 #822Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
KickassTorrents Launches Its Own Release Group
Noticia:As if the site wasn’t drawing enough attention, KAT is now offering its own releases, in filesizes that seem to suggest it is trying to fill part of the void left by the defunct YIFY.
The latest site to jump on the release group bandwagon is KickassTorrents (KAT). Currently the largest torrent site on the Internet, KAT is certainly not short of visitors but it appears that the site believes it can better serve the public with the provision of a site-branded release group.
http://www.hardocp.com/news/2015/12/...p#.VngO3VJv4vc
-
21-12-15, 14:44 #823Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Hello Kitty accounts hacked, 3.3 million users have their details leaked online
Noticia:
Another day, another data breach. This time the victim is sanriotown.com, the official online community for Hello Kitty and another Sanrio characters. Information that includes first and last names, birth dates, countries of origin, gender, and email addresses for 3.3. million accounts – including many that belong to children – have been leaked online.
The information in the leaked database also comes from accounts registered at a number of other Hello Kitty sites, including hellokitty.com, hellokitty.com.sg, hellokitty.com.my, hellokitty.in.th, and mymelody.com.
According to CSO, researcher Chris Vickery discovered the breach. He found "first and last names, birthday [...], gender, country of origin, email addresses, unsalted SHA-1 password hashes, password hint questions, their corresponding answers, and other data points that appear to be website related."
Parents have been advised to change their children’s passwords immediately, as well as their own. And, as is always the case in these situations, to alter the passwords on any other sites they use that share the same login credentials.
Vickery found the leak on Saturday and has notified Sanrio, the owner of the Hello Kitty brand, about the breach. He also notified the ISP being used to host the database. Vickery has not said where he discovered the leaked data in order to reduce the risk of more people accessing it. So far, Sanrio has not commented on the hack.
The report says the data was first compromised on November 22, meaning the hackers have been in possession of the information for almost a month. In addition to changing passwords, it’s recommended that any adults with accounts on the compromised sites set up some kind of credit monitoring.
Sanrio becomes the second company that makes child-focused products to suffer a data breach in the last month. Children’s toy-maker VTech had information on five million customers, including passwords and IP addressess, stolen in November. UK police later arrested a 21-year-old man from Berkshire in connection with the hack.
http://www.techspot.com/news/63206-h...sers-have.html
-
22-12-15, 20:31 #824Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Infrastructure hacking isn't a new thing, New York dam lost in 2013
Noticia:While we wrote that relatively small 'Western Nations' such as Australia are under possible infrastructure hacker threat due to low-security measures, news has come to light that a New York dam was infiltrated by Iranian hackers back in 2013.
With the dam being located no more than 20 miles from New York City, this Iranian hack likely came around thanks to Leon Panetta, ex-Defense Secretary, calling out Iran's hacking prowess in October 2012, putting Governments on high alert for possible hacker threats. With this hack taking place and being kept under the covers until recently, it's just one example of how infrastructure infiltration is a very real threat.
This classified dam is one of the very few public accounts of infrastructure control loss, with all major suppliers of electricity, sewage, water and more all linked to the internet.
http://www.tweaktown.com/news/49138/...013/index.html
-
24-12-15, 14:03 #825Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Unreleased Scripts, TV Shows, Sex Tapes, and IDs of Over 130 Celebrities Stolen
A hacker contacted a famous radio host this month, trying to sell unreleased films of a hit television drama, sex tapes and other memorabilia of over 130 celebrities. All the 23-year old Bahamian hacker wanted was $80,000. Unlike what usually happens, the unnamed host contacted Homeland Security and the latest celebrity hack story totally took the Hollywood turn.

What was stolen in this latest celebrity hack:
Alonzo Knowles, the protagonist of this story hacked into the email accounts of several celebrities by sending them a virus that allowed him to access “a trove of highly guarded entertainment industry secrets sure to rattle the 130 celebrities,” as the NYT puts it. According to reports, the hacker targeted the friends of the celebrities as going after an A-list celebrity directly was difficult. He found their personal information through their friend’s accounts and then sent fake text messages to the celebrities making it seem as though their account had been hacked and needed a password confirmation. Some of these celebrities did respond back with their passwords. In cases where he had “access to their computer,” he simply sent them a virus to gain access to their personal files.
Advertisements
This is just a sample of things I can get. I have more stuff along these lines and can get more if you’re interested.A federal criminal complaint noted that the victim celebrities included movie and TV actors, an A-list singer-songwriter, a casting director, and a hip-hop artist. All of the victims remain unnamed in the complaint. Among the items “available for sale” were scripts of three comedy films, six episodes of a coming season of a hit television series, a hip hop biopic, another television show, social security number of actors and professional athletes, emails and phone numbers of 130 celebrities, and sexually explicit images and videos.
This celebrity hack has happened exactly one year after the Sony Pictures leak. However, the investigators have confirmed that the leaked data is not connected to the last year’s breach. Homeland Security agents negotiated the prices to confirm the presence of sensitive data in an undercover operation. Knowles arrived in Manhattan on Monday from Bahamas to close the deal and was arrested the same day. He appeared in Manhattan Federal District Court on Tuesday and was ordered detained without bail. Knowles is being charged with criminal copyright infringement and identity theft, both of which have a maximum penalty of five years in prison.
Informação da Thread
Users Browsing this Thread
Estão neste momento 2 users a ver esta thread. (0 membros e 2 visitantes)







 Responder com Citação
Responder com Citação


Bookmarks