Lenovo Launches Investigation Into Embarrassing Lizard Squad HackNoticia:Lenovo said it's currently investigating a cyberattack that took the company's website down for several hours earlier this week, though it may not have to look very far. The ornery hacking group known as Lizard Squad is claiming responsibility for the security breach, purportedly as punishment for the recent Superfish scandal.
Let's backtrack a quick moment. Lenovo came under fire earlier this month when it was discovered that a piece of bundled software on consumer laptops and desktops was duping security certificates in order to display ads. Called Superfish, the software is a visual search program that would otherwise be a benign, if not annoying piece of adware, except that it's method of serving ads left users susceptible to man-in-the-middle attacks.
Even worse, users complained that the software would install even if they declined it during first boot, and attempts to uninstall Superfish would leave behind a root certificate. Lenovo ended up apologizing for the incident and also released an automatic software tool to remove Superfish completely, root certificate and all.
Playing the part of judge, jury, and executioner, Lizard Squad apparently decided that Lenovo deserved to be hacked.
"We are reviewing our network security and we will take further appropriate steps to bolster our site and to protect the integrity of our users' information and experience," Lenovo said.
According to KrebsonSecurity, the attack on Lenovo as well as one on Google's Vietnam domain that was also performed by Lizard Squad both were made possible by seizing control over Webnic.cc, the Malaysian registrar that serves both domains and 600,000 others.
In the attack on Lenovo, the Lizard Squad changed the HTML source code to read, "the new and improved rebranded Lenovo website featuring Ryan King and Rory Andrew Godfrey." King and Godfrey used to be part of the now defunct Hack the Planet collective and have since been working to expose Lizard Squad.
It's not yet known how deep Lizard Squad was able to penetrate Lenovo's website and what data it might have stolen, though the organization has said it's planning a data dump for a later time.
http://hothardware.com/news/lenovo-l...ard-squad-hack
User Tag List
 Likes: 0
Likes: 0
Resultados 31 a 41 de 41
-
27-02-15, 17:58 #31Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
-
27-02-15, 17:58 #32Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Lenovo PCs Will Ship Free Of Adware And Bloatware Starting With Windows 10
Noticia:It’s been a rough couple of weeks for Lenovo. The company found itself embroiled in a nasty scandal involving Superfish adware that it installed on consumer notebook and desktop systems. Not only did Superfish hijack encrypted web sessions, but it also left its customers susceptible to man-in-the-middle attacks.
Lenovo offered an apology, issued step-by-step instructions on how to remove Superfish manually, and even released an automated tool to rid systems of the sneaky adware/malware. But the damage was already done; not only did Lenovo’s reputation for making excellent computer systems (especially its ThinkPad range) take a hit, but it now faces a possible class-action lawsuit. And to add insult to injury, Lizard Squad hacked the Lenovo’s homepage earlier this week by exploiting its domain registrar.
But for all the negativity swirling around Lenovo right now, there is some real good coming out of this incident. Lenovo has announced that it is taking to steps to remove all adware and bloatware from its future computers, mirroring a stance that Microsoft has taken with its “Signature Edition” PCs that are sold at Microsoft Stores (online, and brick and mortar).
Future Lenovo computers will only include the operating system plus whatever software is necessary to ensure the proper operation of all included hardware. The company states:
By the time we launch our Windows 10 products, our standard image will only include the operating system and related software, software required to make hardware work well (for example, when we include unique hardware in our devices, like a 3D camera), security software and Lenovo applications. This should eliminate what our industry calls “adware” and “bloatware.” For some countries, certain applications customarily expected by users will also be included.As Lenovo indicates, its customers won’t be able to enjoy this adware/bloatware-free until later this year when Windows 10 launches, but it’s a BIG step that we wish all PC OEMs would take.
http://hothardware.com/news/lenovo-p...ith-windows-10
-
27-02-15, 21:44 #33Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Lenovo promises to be more transparent about pre-installed software
Noticia:Lenovo was busted preloading the Superfish adware software on consumer notebooks, and its customers were clearly not happy. Following its Superfish headache, Lenovo wants to become "the leader in providing cleaner, safer PCs" to its customers.
The company continues trying to repair its public relations nightmare, recently promising a reduction in preloaded applications. In the future, pre-loaded software will include Microsoft Windows, security software, Lenovo applications and programs that must be installed so built-in hardware can function - but Lenovo will list what is installed.
Cybersecurity experts and US government officials said customers should remove Superfish because it leaves users vulnerable to SSL spoofing techniques that can compromise security. Lenovo will also offer a free six-month subscription for the McAfee LiveSafe service, with additional information expected in the next week.
The Superfish adware wasn't installed on ThinkPads, desktops, tablets, smartphones or enterprise server and storage products, the company confirmed.
http://www.tweaktown.com/news/43818/...are/index.html
-
27-02-15, 21:58 #34Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Why Superfish could be the best thing to happen to the PC industry in years
Noticia:
 The Superfish debacle has been an embarrassment and legal concern to Lenovo, a headache to affected customers and yet another concern for the security community. Now that the dust has had time to settle, we’re beginning to see the good emerge as a result of the ordeal.
The Superfish debacle has been an embarrassment and legal concern to Lenovo, a headache to affected customers and yet another concern for the security community. Now that the dust has had time to settle, we’re beginning to see the good emerge as a result of the ordeal.
Lenovo on Friday said the events of the past week have reinforced the principal that customer experience, security and privacy must be their top priorities.
With that in mind, the Chinese computer maker said they will significantly reduce the amount of pre-loaded applications on new systems with the goal of shipping cleaner, safer PCs.

The initiative is starting immediately and by the time they launch Windows 10 products, Lenovo’s standard image will only include the operating system and related software, software to enhance custom hardware (like 3D camera, for example), security software and in-house Lenovo software.
Lenovo added that in some countries, certain applications that are customarily expected by users will also be included. All other software – what the industry often refers to as adware and bloatware – will effectively be eliminated.
The company previous said it would never use Superfish again and has published a removal tool.

The inclusion of bloatware (unwanted programs, toolbars, utilities, games and screensavers) is unfortunately a common practice among computer manufacturers. What happens is software makers approach companies like Lenovo with their wallets open, offering to pay builders in exchange for pre-installing their applications. Although an inconvenience for users, it’s a tradeoff that most have been willing to make in exchange for added revenue.
Granted, not everyone is willing to stoop to such lows for a few extra bucks. Boutique PC builders typically offer a clean installation of Windows while systems sold through the Microsoft Store are classified as Signature Edition meaning they don’t come with bloatware.
Lenovo’s unfortunate incident is a huge opportunity for the rest of the industry and with any luck, it’ll serve as a catalyst for change. It’s time to ditch the bloatware.
http://www.techspot.com/news/59889-w...-industry.html
-
01-03-15, 14:45 #35Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Report: Lenovo only collected $250,000 from Superfish installations
Noticia:Lenovo likely only collected $200,000 up to $250,000 for its Superfish adware installations on consumer PCs, according to a report from Forbes. Previous estimates predicted higher figures - but considering the company's major earnings - the low sum likely won't be worth the legal and public relations headaches.
It is alarming Lenovo, which finalized a deal in summer 2014 to pre-install Superfish, received such a small amount for jeopardizing so much. In addition to promising no more Superfish installations, the company's website was reportedly compromised by the Lizard Squad hacker group last week.
It looks like Lenovo is learning from its mistakes, promising to be more transparent about pre-installed software in the future. For new machines running Microsoft Windows 10, the Lenovo standard image will only include the OS, security software, Lenovo applications, and software/drivers required to make hardware work well.
http://www.tweaktown.com/news/43830/...ons/index.html
-
17-03-15, 10:32 #36Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Microsoft helps Lenovo eradicate the Superfish adware
Noticia:
 Microsoft, Lenovo and other software makers have been working overtime in an effort to eradicate the Superfish adware. The good news is that since the Redmond-based company first got involved, the number of Lenovo machines detecting the vulnerable version of Superfish have dropped dramatically.
Microsoft, Lenovo and other software makers have been working overtime in an effort to eradicate the Superfish adware. The good news is that since the Redmond-based company first got involved, the number of Lenovo machines detecting the vulnerable version of Superfish have dropped dramatically.
Microsoft joined the fight by adding automatic detection of the vulnerable version of Superfish (not all versions are dangerous – just those found on Lenovo machines) to its real-time detection products (think Microsoft Security and Windows Defender).

As the chart above shows, Superfish was detected on just shy of 50,000 machines on February 20. The number peaked at around 60,000 a day later but since that time, infections have been on the decline – dipping heavily on February 24 and February 25.
While Microsoft hasn’t given a specific number as to how many infections they’ve cleared up, the graphic suggests it’s probably somewhere in the 250,000 range.
Of course, Microsoft didn’t take on Superfish on its own. Lenovo ended up releasing its own Superfish removal tool, as did McAfee. Users could also tackle Superfish on their own if they felt so inclined. All things considered, the number of infections was probably much higher than 250,000 but only Lenovo would know for certain.
Superfish is yet another example of why major PC makers need to steer clear of bloatware. Sure, you’re making a few extra bucks by signing distribution deals with software makers but is it really worth trashing your reputation over?
http://www.techspot.com/news/60065-m...sh-adware.html
Que boazinha que é a M$...
-
07-05-15, 08:05 #37Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Lenovo criticized yet again for a major security vulnerability
Noticia:Lenovo, the No. 1 PC manufacturer based on units sold, is being accused of a "massive security risk" that allows hackers to utilize a man-in-the-middle attack to download malware onto victims' systems. Security researchers at IOActive say the vulnerability allows hackers to download malware or hijack the systems themselves.
The flaw takes aim at ThinkPad, ThinkStation and ThinkCenter products, and B, E, K, and V-series models. Lenovo was first alerted to the issue in February, and was given time to release a patch - which was made available last month - before IOActive shared the news publicly.
"An attacker can create a fake [certificate authority] and use it to create a code-signing certificate, which can then be used to sign executables," according to the advisory. "Since the System Update failed to properly validate the certificate authority, the System Update will accept the executables signed by the fake certificate and execute them as a privileged user."
This newest security vulnerability follows just months after Lenovo faced heavy criticism for pre-installing the controversial Superfish adware - and the company later released a patch to help users remove.
http://www.tweaktown.com/news/44987/...ity/index.html
-
12-08-15, 20:39 #38Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Lenovo Accused Of Using ‘Rootkit-Like’ Methods To Sneak Software Onto Clean Windows Installs
Noticia:When acquiring a new notebook or desktop, one of the first things many power users do is wipe it clean. No one likes the "junk" that comes preinstalled, and if time is available, sometimes it's just preferable to start fresh. But what if that was easier said than done? What if that preinstalled junk became more like a plague, persisting even through a fresh install of Windows?
You might think, "That's crazy. Impossible." Well, it is crazy, but it's definitely not impossible.
It seems that installing some asinine malware on customer PCs wasn't enough to satisfy Lenovo's insatiable appetite for intrusion, as it's recently been discovered that the company's installed what's effectively a rootkit onto a range of its notebooks, including Flex and Yoga models.
The root of this problem, no pun, is something called Lenovo Service Engine, in effect low-level firmware that's able to detect whether or not certain files exist in the installed OS. In this case, it seems only Windows 7 and 8 are affected. In the event files this rootkit wants are not present, they'll automatically be fetched from the Internet, and subsequently installed.
Lenovo's goal here is to make sure its customers have the official tools for the sake of keeping up to date and secure - the latter point being humorous given the Superfish debacle. Nonetheless, the way in which the company goes about forcing this on its customers is far from being OK.
Interestingly, Lenovo's implementation is actually kosher with Microsoft, as this is an explicitly laid-out mechanism supported by Windows. Up to this point, though, this is the first known case where that mechanism has been used.
Lenovo has since issued firmware updates to get rid of its Service Engine, although the company hasn't made it a point to highlight it - or the issue in general - to customers. If you own one of the following models, be sure to head to Lenovo's support site and grab the update.
Flex 2 Pro-15/Edge 15 (Broadwell/Haswell models), Flex 3-1470/1570/1120, G40-80/G50-80/G50-80 Touch/V3000, S21e, S41-70/U40-70, S435/M40-35, Yoga 3 14, Yoga 3 11, Y40-80, Z41-70/Z51-70 and Z70-80 / G70-80.
http://hothardware.com/news/lenovo-a...ndows-installs
Outra vez????
Agora com rootkits
-
13-08-15, 14:01 #39Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Lenovo Service Engine further tarnishes company's reputation
Noticia:
Lenovo has found itself at the center of a bloatware-related security controversy once again after a number of users discovered the company was using a little-known feature in Windows 8 and Windows 10 that allows OEMs to embed a Windows executable in their system firmware.
As Ars Technica correctly explains, the feature grants OEMs like Lenovo the ability to load software onto a Windows machine even when a system is wiped clean and a fresh OS installation is performed. Between October 2014 and April of this year, Lenovo allegedly used the technique to install a feature on certain desktops and notebooks it calls Lenovo Service Engine.
Curiously enough, the description of what Lenovo Service Engine does differs on desktops and notebooks.
On desktops, Lenovo claims the software only sends basic information about the system to a Lenovo server and that it only happens once when the system first obtains an Internet connection. On notebooks, Lenovo Service Engine installs OneKey Optimizer which is a firmware, driver and app updater for Lenovo systems.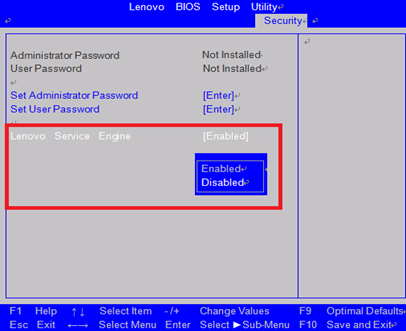
The issue isn’t so much that Lenovo is silently running executables and installing software even on fresh installs of Windows (ok, so maybe it is) but that the Lenovo Service Engine and OneKey Optimizer leave a system open to attack. An Ars Technica forum member found that on Windows 7 systems, Lenovo Service Engine appears to overwrite a Windows system file then creates system services that grab files over unencrypted HTTP.
Lenovo has since stopped including Lenovo Service Engine on new systems and has provided an update to disable it on notebooks and instructions on how to do the same on desktops.
http://www.techspot.com/news/61738-l...eputation.html
-
27-01-16, 09:47 #40Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
New, from the company that brought you SuperFish ...
Noticia:Lenovo chose the third most popular password of 2015 to secure its ShareIT for Windows application and for bonus points have made it hard coded, which there is utterly no excuse for in this day and age. If you aren't familiar with the software, it is another Dropbox type app which allows you to share files and folders, apparently with anyone now that this password ridiculousness has been exposed. As you read on at The Inquirer the story gets even better, files are transferred in the clear without any encryption and it even creates an open WiFi hotspot for you, to make sharing your files even easier for all and sundry. There are more than enough unintentional vulnerabilities in software and hardware, we really don't need companies programming them in on purpose. If you have ShareIT, you should probably DumpIT.
***Update***
We received word that there is an updated version of ShareIT available for those who do use the app and would like to continue to do so.They can also access the latest versions which are posted and available for download on the Lenovo site. The updated Android version of SHAREit is also available for download on the Google Play store. Please visit the Lenovo security advisory page for the latest information and updates: (https://support.lenovo.com/us/en/pro...urity/len_4058) "HOLY COW! Lenovo may have lost its mind. The firm has created vulnerabilities in ShareIT that could be exploited by anyone who can guess that '12345678' could be a password."
"HOLY COW! Lenovo may have lost its mind. The firm has created vulnerabilities in ShareIT that could be exploited by anyone who can guess that '12345678' could be a password."
http://www.pcper.com/news/General-Tech/New-company-brought-you-SuperFish
No minimo ridiculo
-
29-01-16, 15:10 #41Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
One of Lenovo’s Bundled Apps Receives Important Fixes
Noticia:
Lenovo has come under fire not too long ago for a series of important security flaws, especially as far as its bundled apps are concerned. The good news is that the company is actively working to resolve these issues, and one of the most recent apps to receive a fix is ShareIt, which comes bundled with both Lenovo’s Windows and Android-based devices. So if you’re wondering what was wrong with the app in the first place, well it looks like its Windows version included a rather ridiculous password (12345678), which means that anyone on the same Wi-Fi network could have accessed it easily just by taking a wild guess. What’s even worse is that users could not even change this password even if they wanted to.
Then there’s the fact that both versions of ShareIt would send files without encrypting them, and whenever you’d choose to receive some files, the Android version of the app would just create a password-free WiFi hotspot without asking for permission. Lenovo has released updated versions of ShareIt, both of which now include a “secure mode” that encrypts files and asks for a password whenever you want to share them. The problem is that this mode is not implemented by default, which means that it still falls to the user to activate it in order to benefit from protection that should have been there in the first place.
http://www.eteknix.com/one-lenovos-b...portant-fixes/
Informação da Thread
Users Browsing this Thread
Estão neste momento 1 users a ver esta thread. (0 membros e 1 visitantes)







 Responder com Citação
Responder com Citação



Bookmarks