Bem é preciso optimizar a coisa, a bateria que o Chrome come é simplesmente medonha. Com o Safari tenho à vontade mais 2 horas de autonomia no meu MBP.
User Tag List
 Likes: 0
Likes: 0
Resultados 46 a 60 de 80
Tópico: OSX Yosemite
-
13-06-15, 09:45 #46Tech Bencher


- Registo
- Feb 2013
- Posts
- 5,769
- Likes (Dados)
- 0
- Likes (Recebidos)
- 0
- Avaliação
- 5 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Intel i7 5820K - ASRock X99M Killer - 16GB G.Skill DDR4 - Gigabyte GTX 980Ti G1 - Plextor M6e 256GB + Samsung 850 EVO 500GB - Corsair H110 - EVGA G3 750W - Acer 27" 144Hz IPS - Zowie EC2-A - Filco Majestouch 2 TKL - HyperX Cloud II Pro
-
18-06-15, 13:48 #47Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Devastating Xara Exploit Targets OS X Keychain, Exposes User Passwords
Noticia:"Xara" might sound like a cool name for an exploit, but according to researchers at three different US universities, it's one that should cause some alarm. At its root, if Xara is properly exploited, attackers would be able to procure passwords stored in OS X's Keychain, which could be used for most or all of someone's applications.
Specific details are not covered, but it seems that if an app is installed on OS X that takes advantage of this exploit, it can take control of the stored passwords, and other information that might be present (eg: the login username itself). Examples given are hijacking the passwords in Google Chrome, Evernote, WeChat, Facebook, and iCloud.
image: http://hothardware.com/ContentImages...X_Keychain.jpg
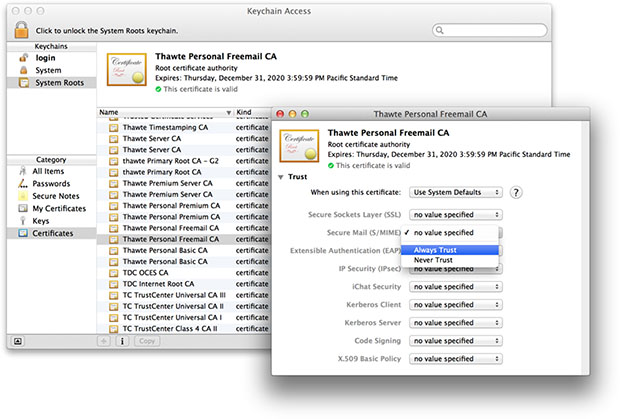 The researchers were successful in exploiting this vulnerability, noting that they were able to hijack both Facebook and iCloud passwords. The ultimate problem is that OS X doesn't verify which application owns which credential set in Keychain, and likewise, there's no mechanism in place to check if saving a credential to another app's keychain is suspicious.
The researchers were successful in exploiting this vulnerability, noting that they were able to hijack both Facebook and iCloud passwords. The ultimate problem is that OS X doesn't verify which application owns which credential set in Keychain, and likewise, there's no mechanism in place to check if saving a credential to another app's keychain is suspicious.
This all sounds horrible, but there is an upside. In order for this exploit to actually gain anything useful, those passwords would have had to have been stored after another application was installed that triggered the exploit. That means that it's highly unlikely that many (or anyone) has fallen prey to this exploit yet, but this is still a major bug that Apple will want to waste little time in patching up.
http://hothardware.com/news/devastat...C68r8VOFUv8.99
-
30-06-15, 19:55 #48Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
The Final Version For OS X 10.10.4 Yosemite Has Been Released
With iOS 8.4 released today, its uncanny for Apple to leave behind OS X. Since iOS 8.4 is the final version of iOS 8, OS X Yosemite has been served with the similar fate. Yes! The final version for OS X Yosemite has been released, 10.10.4 that brings with it a boatload of bug fixes and several enhancements. It is now officially available to the Mac App Store, download your copy immediately.

So what changes are we talking about here? Mostly the changes put in action in the update are under the hood improvements, concerning the daily work in the operating system. Fixes have been done, such as the Wi-Fi related complains that Apple has been getting for quite a while. Henceforth, networking has been improved. Lets head down to see some more details over the update.
OS X 10.10.4 Update Brings A Raft Of Bug Fixes And Stability
The issues prevailing for users who connect external displays and panels details are finally put to rest. For users who use Migration Assistance, the update has washed it with an ample bug fixture and the workings will be more secure yet reliable than ever. Overall, the raft of bug fixes is concerned with enhancing the functionality of users and improving stability in an all rounder approach. The entire changelog as of Mac App Store is as follows:
The OS X Yosemite v10.10.4 update improves the stability, compatibility, and security of your Mac.Don’t worry, editors are not left out for fixes as well. Aperture and iPhotos have also been fixed pertaining to the issues that involves library content transfers to the new Photos App for Mac. The syncing operation has also been made more reliable for the user in the iCloud Photo Library. By all means, OS X Yosemite users will definitely feel an overall change in the operation of several actions and app operation reliability.
This update:
– Improves networking reliability
– Improves Migration Assistant reliability
– Addresses an issue that prevented some external displays from functioning properly
– Improves the reliability of upgrading iPhoto and Aperture libraries to Photos
– Improves reliability when syncing photos and videos to iCloud Photo Library
– Addresses an issue that could cause Photos to unexpectedly quit after importing some Lecia DNG files
– Resolves an issue that could delay outgoing email messages in Mail
– Fixes an issue where a website could prevent the user from navigating away by presenting repeated JavaScript alerts in Safari
It is highly recommended for users to download the OS X 10.10.4 Yosemite update as it brings a lot of stability and fixes for the system. You can update your OS X by going to the Mac App Store and navigate to the update tab and wait for a while. When the update 10.10.4 is prompted, install it. The size of the update is a mere 1.09GB. Give the update a swirl and let us know about your experience in the comments.
-
13-07-15, 16:51 #49Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
OS X 10.10.4 SMTP Mail Error Fix – How To
Shortly after the release of OS X 10.10.4 and iOS 8.4, users have faced several issues with irregular intervals of account connection and inability to send email via specific servers while In other cases a complete Mail shutdown have been experienced. If you guys came across such issues, you’re not alone. Gmail account holders are the primary affected users who started noticing such issues in a sporadic manner after upgrading their OS to the latest version.

Apple’s support forums were piling up with complaints for the following issue until a day later the tech company took notice of it and provided a technical account. Apple stated that both operating systems are integrated with increased security opposing to a ‘Logjam’ named TLS vulnerability. The novelty introduced for more security disabled users with updated operating systems to connect to weak encryption.
Fix SMTP Mail Issue On OS X 10.10.4
The result of this adverse security enhancement is users inability to connect to SMPT connections, HTTPS webpages and connecting to certain enterprise class Wi-Fi (802.1X) networks. The fix does not involve another update from Apple but changing several settings to enable behave in an appropriate and adequate manner as it is supposed to be. The following steps are as follows:
Step 1:
Launch the stock Mail App on OS X and click on ‘Mail’ and then further proceeding to ‘Preferences’.

Step 2:
In the Preferences Window, click on ‘Accounts’ and then select the account that is causing issues. Once you do that, proceed to the ‘Advanced Tab’.

Step 3:
Toggle the check box for ‘Automatically detect and maintain account settings’ and restart the Mail app.

Step 4:
Once you open the Mail app again and make sure it is still checked after the restart process.
This is it for the fix for issues on Mail. This may not be the most accurate of ways to fix the problem. The fix remains limited to the OS X platform alone and not iOS. Fix for iOS may arrive soon which too will have the same steps involved to trigger the addition of accounts. Do take note and backup your data before deleting email data. This is it for now, let us know if this fix worked out for you.
-
16-07-15, 17:37 #50Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Apple Releases First Public Beta For OS X 10.10.5 To Testers
The final few versions of Yosemite are prevailing through beta versions before the arrival of El Capitan later this fall. A few days ago, Apple seeded OS X 10.10.5 to developers and recently the course shifted to a public beta release. Considering the launch of El Capitan, this may be one of the important updates to Yosemite. There are a lot of significant changes yet to be introduced before Apple puts ground to its forthcoming OS X update.

If you want to update to the OS X 10.10.5, it is available through Software Update Mechanism via Mac App Store. Do make sure that you are enrolled for the Apple Beta Software Program that will enable you to get the update. The public beta for OS X 10.10.5 carries the same build number (14F6a) that was seeded to developers a few days back. Lets see if there are any changes introduced in the public release.
OS X 10.10.5 Public Beta Released – No Major Upgrade
Since the two builds are the same, public beta and developer beta, there may not be a major jump in upgrades. It seems that OS X 10.10.5 public beta does not constitute any major visual differences and performance enhancements but it does seem likely that there is improved stability in the overall OS. Since testers would be keen to notify any major bug fixes, it is presumed that Apple will forward this build as the final release as OS X 10.10.5 Yosemite.
It is also to be taken in to account that some users reported about the first beta of OS X 10.10.5 not showing in the Software Update Program after the release on Tuesday. However, as we speak, the beta has now appeared and all ready to be downloaded for testing purposes. It can be presumed that OS X 10.10.5 will be the last version of Yosemite before El Capitan is introduced.
OS X 10.10.4 was released on 30th June alongside Apple’s newest mobile platform iOS 8.4. It hosted under the hood improvements in terms of performance and ample of bug fixes for more stability. The troubling Discoveryd process was also removed. The final release date for OS X 10.10.5 has yet not been announced but we will notify you as soon as it arrives, This is it for now, download the public beta and let us know if you see any major changes according to your experience.
-
23-07-15, 16:57 #51Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
OS X 10.10 hit by privilege escalation vulnerability
Noticia: Apple's OS X 10.10 has been found to contain a serious privilege escalation vulnerability, fixed in the company's upcoming OS X 10.11 El Capitan.
Apple's OS X 10.10 has been found to contain a serious privilege escalation vulnerability, fixed in the company's upcoming OS X 10.11 El Capitan.
Security researchers have uncovered a serious vulnerability in Apple's OS X 10.10 Yosemite operating system, allowing unprivileged users to exploit an error logging system to gain administrative privileges.
Introduced in OS X 10.10 to make developers' lives easier, the environment variable DYLD_PRINT_TO_FILE was designed to give the dyld dynamic linking tool the ability to log error messages to any arbitrary file for later review, rather than the standard error output (stderr). Unfortunately, there's a rather serious flaw in the way it operates: improperly used, the environment variable allows dyld to write to any arbitrary file on the system - including files unprivileged users should not be able to touch, such as the password file.
According to a write-up of the flaw by security researcher Stefan Esser, exploitation of the flaw is trivial: a test can be carried out by running the one-line command 'EDITOR=/usr/bin/true DYLD_PRINT_TO_FILE=/this_system_is_vulnerable crontab -e', which creates a file in the core directory of the system with root permissions, regardless of the permissions of the user who ran the command. More seriously, demonstrated exploits for the vulnerability include removing password permissions from arbitrary root-level user accounts and overwriting any binary on the system with malicious code.
Apple has yet to respond to the report, which has shown the vulnerability to work on even the latest OS X 10.10 Beta 5 but to not be present on OS X 10.11 Beta 1 or Beta 2. 'Because it will likely take months for Apple to react to this issue we released a kernel extension that protects from this vulnerability by stopping all DYLD_ environment variables form being recognized by the dynamic linker for SUID root binaries,' Esser wrote. 'In addition to that it adds a mitigation against a common trick to circumvent O_APPEND restrictions on file descriptors.'
Esser's SUIDGuard tool can be found on its GitHub repository.
http://www.bit-tech.net/news/bits/20...ulnerability/1
-
24-07-15, 16:51 #52Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Apple inserts bug into OSX
Noticia:
Allows designer malware
The software genii at Apple have redesigned their OSX software to allow malware makers to make designer micro-software that can infect Macs with rootkits.
Obviously the feature is one that Apple software experts designed specifically for malware writers, perhaps seeing them as an untapped market.
The bug in the latest version of Apple's OS X allows attackers root user privileges with a micro code which could be packed into a message.
Security researcher Stefan Esser said that this was the security hole attackers regularly exploit to bypass security protections built into modern operating systems and applications.
The OS X privilege-escalation flaw stems from new error-logging features that Apple added to OS X 10.10. Plainly the software genii did not believe that standard safeguards involving additions to the OS X dynamic linker dyld applied to them because they were protected from harm by Steve Job's ghost.
This means that attackers to open or create files with root privileges that can reside anywhere in the OS X file system.
"This is obviously a problem, because it allows the creation or opening (for writing) of any file in the filesystem. And because the log file is never closed by dyld and the file is not opened with the close on exec flag the opened file descriptor is inherited by child processes of SUID binaries. This can be easily exploited for privilege-escalation," Esser said.The vulnerability is present in both the current 10.10.4 (Yosemite) version of OS X and the current beta version of 10.10.5. Importantly, the current beta version of 10.11 is free of the flaw, an indication that Apple developers may already be aware of the vulnerability.
An Apple spokesman said that engineers are aware of Esser's post of course they did not say they would do anything about it. They will have to go through the extensional crisis involved in realising that their product was not secure or perfect. Then the security team will have to issue orders, signed in triplicate, sent in, sent back, queried, lost, found, subjected to an internal inquiry, lost again, and finally bury it in soft peat for three months and recycled as firelighters.
http://www.fudzilla.com/news/38307-a...s-bug-into-osx
-
30-07-15, 09:58 #53Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Safety First – An All New Fake Safari Update Puts OS X Users At Great Risk
Apple, iOS and OS are known for quite a bit of things. One of these is security, and it’s one of the top features that cause many to stick to Apple devices. That however does not mean that flaws do not occur. In fact, we’ve seen several occur so far, which have put a lot of users at risk. Another one has just been discovered on the Mac, so read below to find out if you’re one of the affected or just to simply warn others.

Latest Mac Vulnerability Can Lead To User Security Risk Discover Researchers
Folks over at Malwarebytes are as active as ever and they’ve recently uncovered a new Mac vulnerability that could affect countless users, and might have already affected countless many. According to them, they have seen several websites pushing Safari updates which not only aren’t from Apple, but also install some unwanted programs on your computer.
InstallCore Installer, which is known to cause problems for Mac users, is now disguising itself in new ways to fool you. Several sites, with programs built to install the software on your computer, now present this installer disguised as a Safari update, which is of course fake in nature. Installing this update ends up installing MacKeeper and ZipCloud on your device.
The way this works is that you’re forced to accept installation for both the programs, and after installation several factors on your device are affected. While you can read it in detail above, the short details involve preferences for Chrome and Firefox being changed and installation of new Safari support files that completely mess up existing installation of Apple’s browsers.
So if you’re carried out this process yourself, or know anyone who might have, warn them and proceed towards not only removing both MacKeeper and ZipCloud but also towards carrying out a fresh OS X installation. Stay tuned, and let us know what you think in the comments section below.
Noticia:
http://wccftech.com/fake-safari-update/#ixzz3hMpP7BJc
-
30-07-15, 17:12 #54Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Download: Reeder 3 Public Beta For Mac OS X For Free
Reeder 3 public beta for Mac OS X Yosemite is now available to download. The freshly released beta build for users is absolutely free to try.

With the sad demise of Google Reader, many third-party RSS alternatives have picked up momentum in the mobile and desktop space. If you take your RSS very seriously, then you would already know that how much popular Feedly and Reeder actually are, with the latter having a big following of its own, although currently only available on iOS and OS X. Today, the company has officially revealed its future plan for the Mac with the release of Reeder 3 public beta for those running OS X Yosemite.
The first thing you’ll notice when you launch the newly designed Reeder 3 app is the interface. Designed to fit well with Apple’s modern UI aesthetics, users can expect plenty of blurs and sharply used fonts throughout. Apart from that, the app looks far more cleaner than before and there’s definitely less clutter, so the user can focus more on the content they’re reading rather than the machinery that’s churning stuff out.
Reeder 3 supports all of the modern news reading services, and the list includes:
- Feedbin
- Feedly
- Feed Wrangler
- FeedHQ
- NewsBlur
- The Old Reader
- Inoreader
- Minimal Reader
- BarQux Reader

If you’re asking us, we’d give Feedly the thumbs up the most in the list of supported news reading services, but of course, your preference may vary.
Reeder 3 also supports read later services, and integrates the two big names on Web, which are:
- Readability
- Instapaper
Both of the services integrate really well with the app, and makes consuming content a tad bit better.

Since Reeder 3 is beta software, there are things that can go ‘wrong’ during your everyday usage routine. Expect crashes from time to time, and maybe a stutter or two at least expected moments. And like we mentioned before, Reeder 3 is in public beta and is absolutely free to download and try.
You can download the first beta of Reeder 3 from Reeder’s official website from here. Be sure to go through the changelog first in order to find out what will and might not work for you.

If you do happen to take Reeder 3 beta for a spin, then be sure to let us know what you think about it in the comments section below. And oh, make sure you add us to your RSS feed as well, to keep yourself updated on our coverage.
-
02-08-15, 13:07 #55Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
TaiG iOS 8.4 Jailbreak For Mac OS X Now Available
You can now download TaiG iOS 8.4 jailbreak tool for Mac OS X. Previously the tool was exclusive to Windows but is now available to those who are in the ownership of an OS X powered computer.

The newly released TaiG iOS 8.4 jailbreak tool for OS X carries the same features as its Windows counterpart. In short, if you’ve already jailbroken with TaiG using the Windows version of the tool, then you’re good to go and can skip this release altogether. But if you’re starting away fresh, then we’ll explain to you in simple words how you can go about the process.
The process is exactly the same as how it was on Windows. First and foremost, download the Mac version of the TaiG tool from the download link at the end of this post. Once you’re done downloading, simply launch it on your Mac by right clicking on the TaiG file in the Applications folder and then clicking on ‘Open.’ Once the tool is up and running, simply plug in your device to your Mac using a USB cable and you’re all good to go.

Do note one thing though, you’ll need to turn off the passcode and Find my iPhone features on your iPhone or iPad before you can go forward, otherwise the tool will simply fail to work. You can disable the passcode feature by going to Settings > Touch ID & Passcode and then tap on the ‘Turn Passcode Off’ button. You can disable Find my iPhone by going to Settings > iCloud > Find my iPhone and from here toggle the ‘Find my iPhone’ button to the OFF position. You’ll be required to enter your iCloud password to confirm the action.

It’s also recommended that you disconnect your Apple Watch from your iPhone before going ahead with the jailbreak process. The connection between the two devices does seem to hamper with the jailbreak, as we have seen in the past, so we highly recommend that you turn off Bluetooth on your iPhone, and put your Apple Watch in airplane mode before going ahead.
You can download the TaiG iOS 8.4 jailbreak tool for Mac OS X from this link. And if you’re jialbreaking for the first time, then you can follow our guide posted here for more details.
If you’ve jailbroken your iOS device using the recently released PP jailbreak tool, then you can skip on TaiG for Mac as well.
TaiG supports all devices on iOS 8.4, and that includes the latest iPod touch 6 which was recently released by Apple a few days back.
-
04-08-15, 17:42 #56Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
OS X privilege escalation exploit makes for silent-killer malware
Noticia:A zero-day vulnerability in OS X Yosemite has been exploited in the wild, and it's a doozy. According to Malwarebytes, a script that exploits the vulnerability can give a user root privileges without the need for a password prompt, which then allows malware running under that user's account to do untold harm to a vulnerable Mac.
OS X (as well as other *nix operating systems) maintains a list of users who can access root privileges, called sudoers. The script in question uses the vulnerability, called DYLD_PRINT_TO_FILE, to modify the sudoers file to grant those users root permissions without being prompted for a password. Once the script modifies the sudoers list, it's free to do whatever root-level actions sudoers allows without the victim seeing any password prompts.
Malwarebytes researcher Adam Thomas found that this issue is being exploited in the wild. An app called VSInstaller uses the vulnerability to make the required modifications to sudoers before installing one or more potentially-unwanted programs without any prompts. To cover its tracks, the script then deletes itself and performs an innocuous action, like opening the page for an unrelated app on the Mac App Store.
Stefan Esser, the iOS-jailbreak developer known as i0n1c, blogged about the exploit without notifying Apple. Fortunately, a separate researcher had already discovered the issue and notified Apple, so the Mac maker wasn't caught completely by surprise. Esser has provided a fix of his own, but Malwarebytes seems skeptical of both the update and Esser's motives.
Apple has not yet patched the vulnerability. Hopefully, with adware exploiting this hole in the wild, the company will move to squash it quickly.
http://techreport.com/news/28748/os-...killer-malware
-
05-08-15, 08:28 #57Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Macs Are Vulnerable to Attacks Due to a Serious OS X Flaw
Noticia:
Software companies are usually pretty good at protecting their products from hacker attacks, but they sometimes overlook some flaws that end up leaving systems vulnerable. We’ve seen it before with Windows and Android, and now it’s OS X’s turn to join the fold, as its latest version apparently includes a serious flaw that can be used by hackers to attack a user’s computer without even needing a password. The flaw is related to a hidden document named Sudoers, which contains a list of software-related permissions. Yosemite stores the list in such a way that allows hackers to actually add malware into the register.
The problem was detected by well-known iOS jailbreaker Stefan Esser, who is now facing some accusations from Apple for revealing the news before telling the company. Stefan also went ahead and created a kernel extension that could help you protect your Mac until Apple releases an official fix. Since we’re talking about a very serious vulnerability here, it probably won’t take Apple too long to fix it. However, if you want to try out Stefan’s solution you can go ahead and download it right here. I’d probably just wait for an official patch, though.
Thank you Engadget for providing us with this information.
http://www.eteknix.com/macs-vulnerab...ous-os-x-flaw/
-
05-08-15, 14:04 #58Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
OS X 10.10.5 to Fix Thunderstrike 2 and Zero-Day DYLD Vulnerabilities
Apple aims to patch the Thunderstrike 2 exploit in Mac OS X “as soon as possible,” as the worm can only be fixed by re-flashing your firmware chip once it infects your computer.

This promise comes only days after the firmware worm was made public by a team of security researchers and shows how critical this concern is for the security of Apple’s desktop and laptop computers. Reports claim that Thunderstrike 2 has already been partially patched in Mac OS X 10.10.4 update. This worm allows attackers to overwrite a computer’s firmware using a malicious webpage and cannot be killed even by reinstalling OS X or reinstalling a new hard drive. This worm essentially turns your machine into an incurable state. While it has been partially patched in the last OS X update, its ability to spread from one computer to others remains unpatched.
More concerning that Thunderstrike 2 is, however, another security vulnerability that Apple is focusing to send the patch for. Next update to Apple’s desktop operating system will reportedly bring the patch to a zero-day bug titled DYLD which is a serious privilege escalation bug. This vulnerability allows a program to run as an administrator bypassing the security measures including passwords, ending up installing crapware on your Macs. Initial beta of this update didn’t include a fix for the issue, however, Mac OS X 10.10.5 will be bringing the patch, according to the Guardian.
While the company sends patches of both these vulnerabilities discovered in Mac OS X, “Apple has taken interim measures to prevent further exploitation of the vulnerability, including revoking the credentials of developers who use it, and including any app which does so on the company’s regularly updated list of malware,” reports the Guardian. Apple has always used the security of its devices as a major marketing and selling point. Comparing the security with its competitors, the tech company has long highlighted the security features of OS X in its ad campaigns.
With two back to back vulnerabilities, Apple seems to be losing its lead in security as the Macs are facing some highly advanced hacking and exploiting techniques used by attackers. Currently in the public eye, Apple is expected to take swift action to patch these vulnerabilities and take the security of its Macs a notch higher.
-
09-08-15, 13:05 #59Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Fix Fetching Issue In Mac OS X ‘Open With’ Context Menu – How To
Here’s how you can fix Fetching issue in Mac OS X ‘Open With’ context menu. The fix is rather simple, and can be implemented immediately by any type of user.

As you keep on using your Mac, different files start to accumulate in the background, making the overall experience a rather slower one compared to how it was on day one. That’s completely normal, and something that happens on every desktop level OS, including Windows and Linux. But things start to get frustrating when the most used features or options in a particular OS start to show signs of slowing down, which in turns shoots down productivity. Case in point, OS X users will be aware of the ‘Fetching’ message that appears when you right-click on something then hover your mouse pointer over the ‘Open With’ context menu. At times, the message will seize to go away, but if you close down the context menu and hover your mouse again over the ‘Open With’ menu, then things turn normal on their own.
What sorcery is this? And how can you fix it? Glad you asked, and we’ll walk you through the process which is a simple command line which you have to enter in Terminal.
Fix ‘Fetching’ Issue In Mac OS X ‘Open With’ Context Menu
1. Launch the Terminal app. Simply bring up Spotlight search and search for ‘Terminal.’

2. Now enter the following line exactly as it is in Terminal:
/System/Library/Frameworks/CoreServices.framework/Versions/A/Frameworks/LaunchServices.framework/Versions/A/Support/lsregister -kill -seed -r -f -v -domain local -domain user -domain system
3. Press the ‘Return’ key on your keyboard to confirm.
Let Terminal do its thing, and the process can take up to a minute. But once done, the ‘Fetching’ issue will be long gone.
The command line you entered above basically resets the Launch Services, making things how they were when you installed OS X for the first time. We also suggest that you save the above command line for later as well, if the issue starts to arise. And yes, using the command line is absolutely safe, so users shouldn’t worry about anything at all.
Coming back to files accumulating in the background bit we mentioned earlier – if you want to remove an app and all of its leftover settings, then be sure to check out: How To Completely Remove A Mac App And All Of Its Settings.
It’s always a good idea to keep on tuning up your Mac from time to time, folks. You might never know when things would go down.
-
13-08-15, 12:45 #60Tech Ubër-Dominus


- Registo
- Nov 2013
- Local
- City 17
- Posts
- 30,121
- Likes (Dados)
- 0
- Likes (Recebidos)
- 2
- Avaliação
- 1 (100%)
- Mentioned
- 0 Post(s)
- Tagged
- 0 Thread(s)
Boot Camp 6 With Windows 10 Support Now Available For Mac OS X
Apple has released a new and updated version of Boot Camp that fully supports Microsoft’s latest OS – Windows 10.

If you want to install Windows on a Mac, then Boot Camp is the way to go, and Apple has long since supported the installation of Microsoft’s desktop OS on its hardware using the magic of its very own aforementioned software. And now, the Cupertino giant has released a new update to Boot Camp, pushing it to version 6, which brings with it full support for Windows 10.
It’s also worth noting at this point that users will older Mac models might be out of luck running Windows 10 on their machines. The full list of supported Macs is as follows, according to Apple’s official support document:

If your Mac is not listed above, then you’re well out of luck running Windows 10 on your machine. And if you want to find out which year your Mac originated from, along with the model, then follow the steps given below:
1. Click on the Apple logo on the Mac menu bar.
2. Now click on ‘About this Mac.’

3. The first line in the list of specs represents the year from which your Mac originated from and the model as well. Hence, if your Mac is in the above list then you’re well and good, if not then you’re out of luck.

Boot Camp 6 is only supported on compatible Macs with Yosemite installed, which means Windows 10 can’t be installed on your computer if you’re running an older version of OS X on top. Yosemite is a free upgrade and we recommend users to make the leap towards it.
Boot Camp 6 supports both 32 and 64-bit versions of Windows 10, hence you can rest assured that you’ll be well covered in that regard. Furthermore, the copy of Windows 10 you’re going to be installing on your Mac must be legit, which is a given. And if you already have Windows 7, 8 or 8.1 installed on your Mac, then you can upgrade to Windows 10 absolutely free, provided you have all the necessary updates installed beforehand.
Boot Camp 6 brings in support for the following:
- USB 3
- USB-C on the MacBook (Retina, 12-inch, Early 2015)
- Thunderbolt
- built-in SD or SDXC card slot
- built-in or USB Apple SuperDrive
- your Apple keyboard, trackpad, and mouse
The Boot Camp 6 update is still propagating through and might not be available to everyone worldwide, so hang in there tight till the update hits your Mac.
All set to install Windows 10 on your Mac? Then be sure to check out: How to Install Windows 10 on Mac: Dual-Boot & VM Guides.
Source
Informação da Thread
Users Browsing this Thread
Estão neste momento 1 users a ver esta thread. (0 membros e 1 visitantes)





 Responder com Citação
Responder com Citação


Bookmarks